Installing Oracle Fusion Applications > Setting up Identity and Access Management Node > Perform Post-Provisioning Configuration
Previous: Provision Identity Management
Pro Oracle Fusion Applications – Installation and Administration
Now you can buy the first and only comprehensive book on Oracle Fusion Applications Installation and Administration which covers end to end information on introduction, planning, installation and troubleshooting guides for implementing Fusion Applications on premise. Buy it now from any of the following stores.
http://www.amazon.com/Pro-Oracle-Fusion-Applications-Administration/dp/1484209842
http://www.barnesandnoble.com/w/pro-oracle-fusion-applications-tushar-thakker/1121094340
http://www.apress.com/9781484209844
http://www.springer.com/us/book/9781484209844
Correcting Datasource Configuration
Due to Bugs 17075699 and 17076033 in Identity Management Provisioning, you must make changes to the following datasources:
- EDNLocalTxDataSource*
- mds-oim*
- mds-owsm*
- mds-soa*
- oamDS*
- oimJMSStoreDS*
- OraSDPMDataSource*
- SOALocalTxDataSource*
To make the changes, proceed as follows:
1. Log in to the WebLogic Administration Console at http://idmhost.paramlabs.com:7777/console
Use weblogic_idm username and password which you provided before provisioning.
2. Click Lock & Edit.
3. Navigate to Services -> Data Sources
4. Click on the data source to be updated, for example, EDNLocalTxDataSource
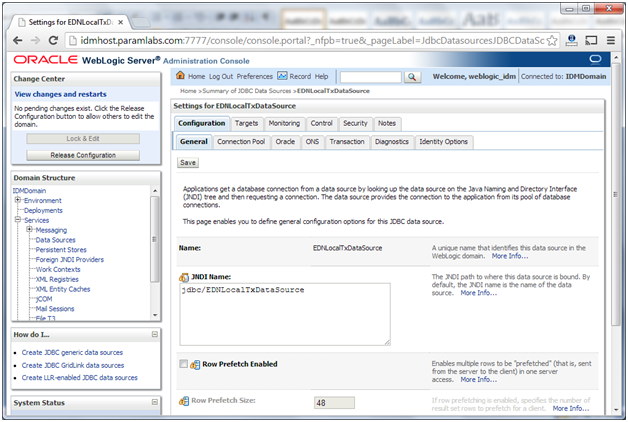
5. Click the Transaction tab
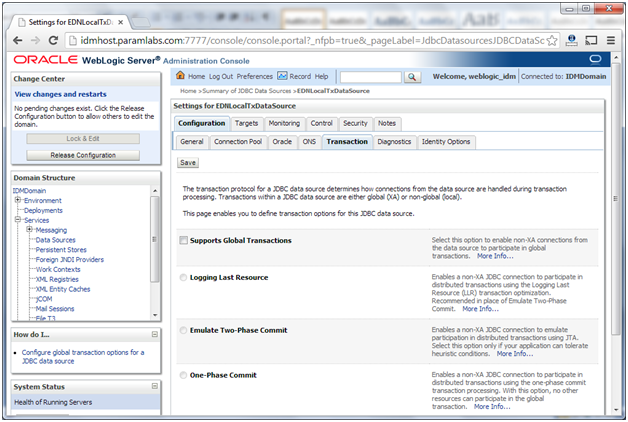
6. Deselect Supports Global Transactions if not already deselected. In our case it is already deselected.
7. Click Save.
8. Repeat Steps 4 through 7 for all the listed datasources.
Note: We had to change the checkbox only or oamDS. All other were already deselected.
9. Click Activate Changes.
10. Restart all servers.
Updating Oracle HTTP Server Runtime Parameters
By default, the Oracle HTTP Server contains parameter values that are suitable for most applications. These values, however, must be adjusted in IDM Deployments
Proceed as follows:
1. Edit the file httpd.conf, which is located in: WEB_ORACLE_INSTANCE/config/OHS/component_name
[fusion@idmhost ~]$ cd /app/oracle/config/instances/ohs1/config/OHS/ohs1/
[fusion@idmhost ohs1]$ cp -pr httpd.conf httpd.conf.bak
[fusion@idmhost ohs1]$ vi httpd.conf
2. Find the entry that looks like this:
<IfModule mpm_worker_module>
3. Update the values in this section as follows:
<IfModule mpm_worker_module>
ServerLimit 20
MaxClients 1000
MinSpareThreads 200
MaxSpareThreads 800
ThreadsPerChild 50
MaxRequestsPerChild 10000
AcceptMutex fcntl
</IfModule>
4. Leave all remaining values unchanged.
5. Save the file.
[fusion@idmhost ohs1]$ diff httpd.conf httpd.conf.bak
164,169c164,168
< ServerLimit 20
< MaxClients 1000
< MinSpareThreads 200
< MaxSpareThreads 800
< ThreadsPerChild 50
< MaxRequestsPerChild 10000
—
> MaxClients 150
> MinSpareThreads 25
> MaxSpareThreads 75
> ThreadsPerChild 25
> MaxRequestsPerChild 0
1036c1035
< include “/app/oracle/config/instances/ohs1/config/OHS/ohs1/webgate.conf”
—
> include “/app/oracle/config/instances/ohs1/config/OHS/ohs1/webgate.conf”
\ No newline at end of file
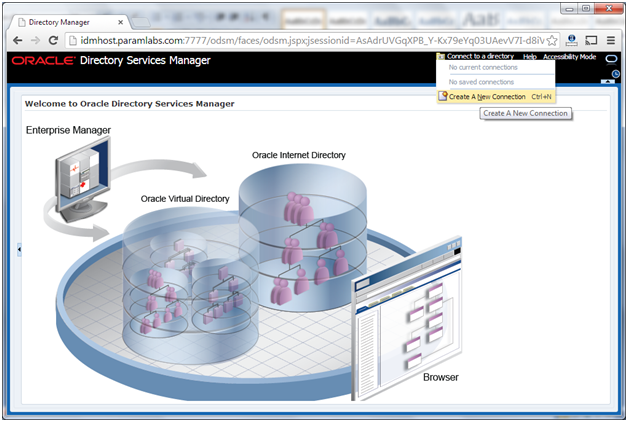
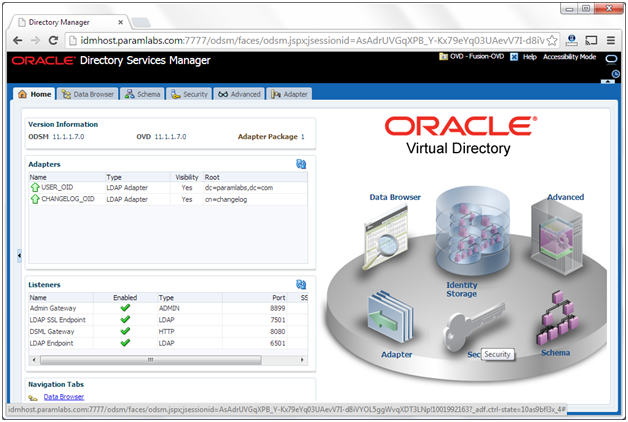
Creating ODSM Connections to Oracle Virtual Directory
Before you can manage Oracle Virtual Directory you must create connections from ODSM to each of your Oracle Virtual Directory instances. To do this, proceed as follows:
1. Access ODSM at: http://idmhost.paramlabs.com:7777/odsm
2. Follow these steps to create connections to Oracle Virtual Directory:
To create connections to Oracle Virtual Directory, follow these steps. Create connections to each Oracle Virtual Directory node separately. Using the Oracle Virtual Directory load balancer virtual host from ODSM is not supported:
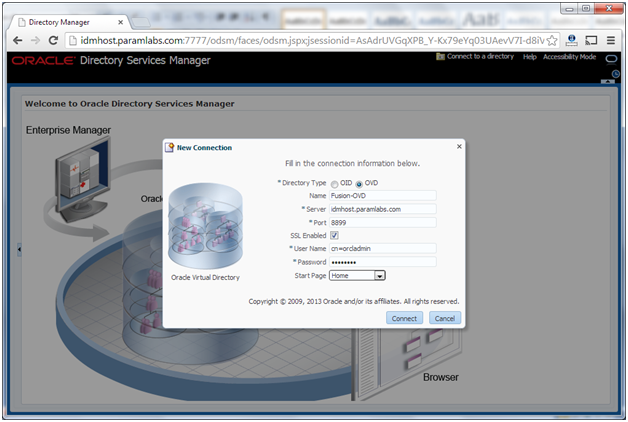
Create a direct connection to Oracle Virtual Directory on idmhost providing the following information in ODSM:
Host: idmhost.paramlabs.com
Port: 8899 (The Oracle Virtual Directory proxy port, OVD_ADMIN_PORT)
Enable the SSL option.
User: cn=orcladmin
Password: password_to_connect_to_OVD
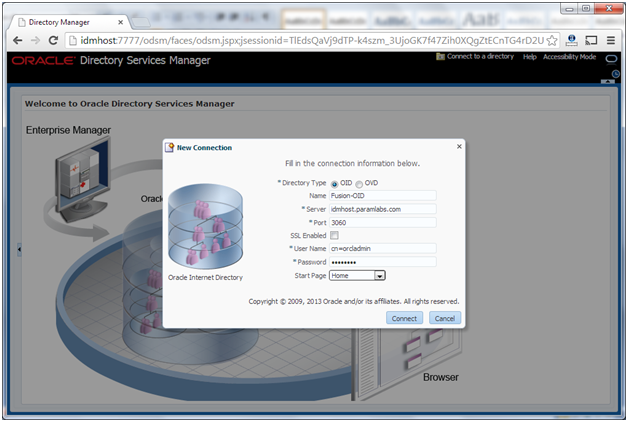
Creating ODSM Connections to Oracle Internet Directory
Before you can manage Oracle Internet Directory you must create connections from ODSM to each of your Oracle Internet Directory instances. To do this, proceed as follows:
1. Access ODSM at: http://idmhost.paramlabs.com:7777/odsm
2. Follow these steps to create connections to Oracle Internet Directory:
To create connections to Oracle Internet Directory, follow these steps.
Create a direct connection to Oracle Internet Directory on idmhost providing the following information in ODSM:
Host: idmhost.paramlabs.com
Port: 3060
Deselect the SSL option.
User: cn=orcladmin
Password: password_to_connect_to_OID
Post-Provisioning Steps for Oracle Identity Manager
Perform the following task to ensure that Oracle Identity Manager works correctly after provisioning.
Add an Oracle Identity Manager Property
As a workaround for a bug in the Identity Management Provisioning tools (Bug 16667037), you must add an Oracle Identity Manager property. Perform the following steps:
1. Log in to the WebLogic Console.
2. Navigate to Environment -> Servers.
3. Click Lock and Edit.
4. Click on the server wls_oim1
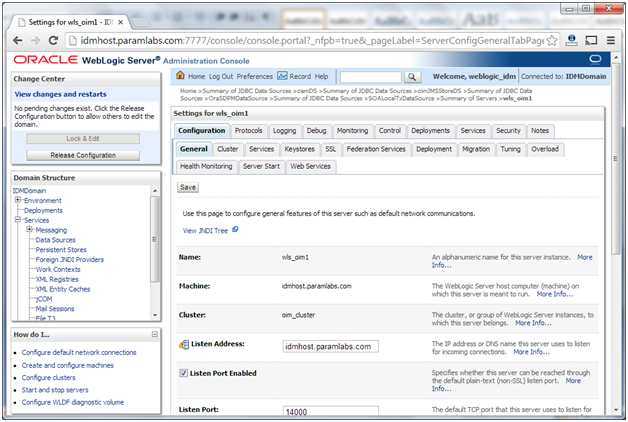
5. Click on the Server Start subtab
6. Add the following to the Arguments field:
-Djava.net.preferIPv4Stack=true
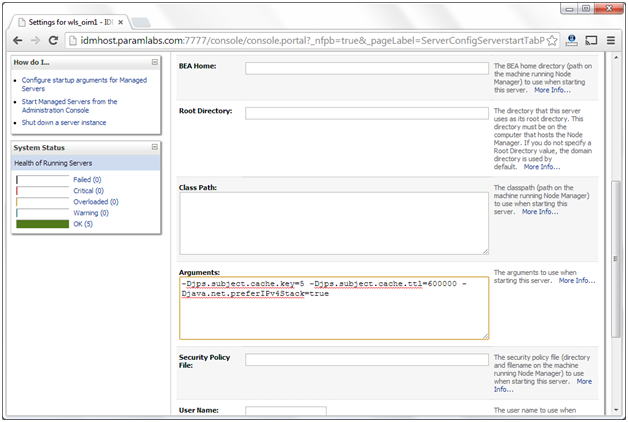
7. Click Save.
9. Click Activate Changes.
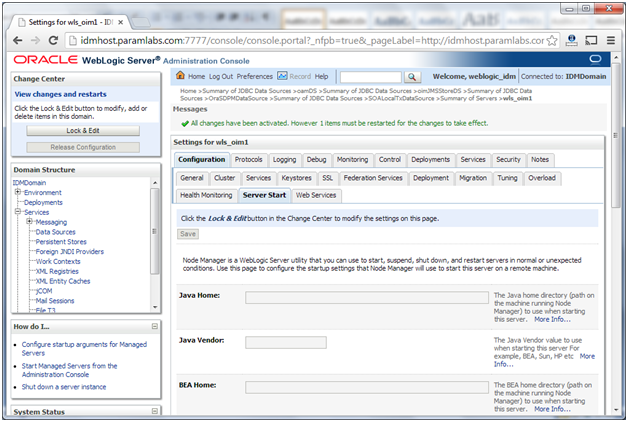
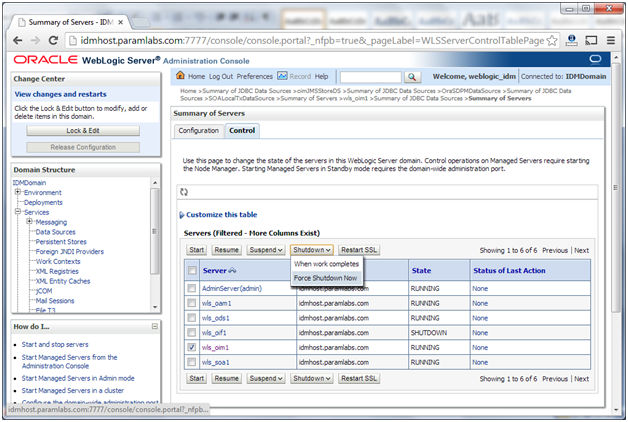
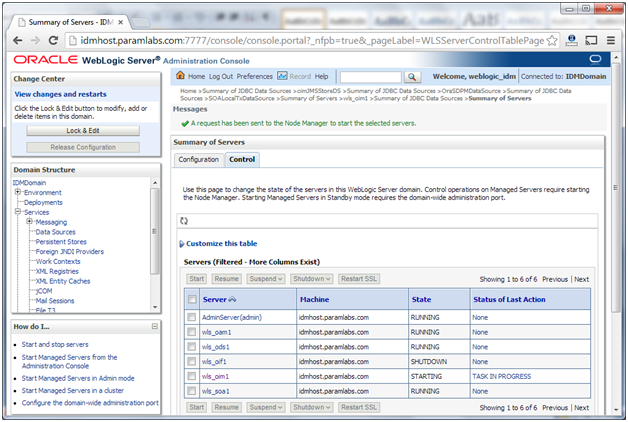
10. Restart the managed server wls_oim1
Post-Provisioning Steps for Oracle Access Manager
Updating Existing WebGate Agents
Update the OAM Security Model of all WebGate profiles, with the exception of Webgate_IDM and Webgate_IDM_11g, which should already be set
To do this, perform the following steps:
1. Log in to the Oracle Access Manager Console as the Oracle Access Manager Administration user (oamadmin)
http://idmhost.paramlabs.com:7777/oamconsole
2. Click the System Configuration tab.
3. Expand Access Manager Settings – SSO Agents.
4. Click OAM Agents and select Open from the Actions menu.
5. In the Search window, click Search.
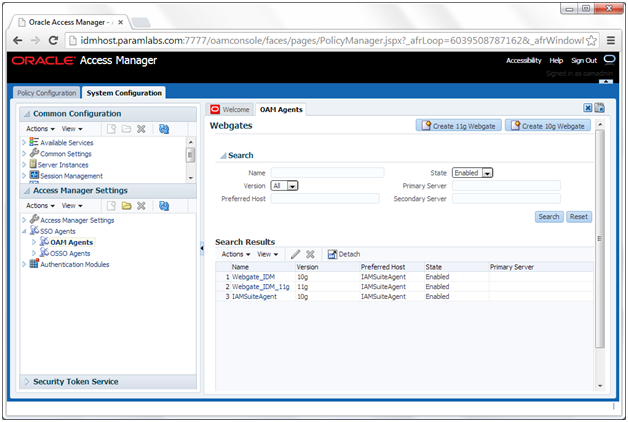
6. Click an Agent, for example: IAMSuiteAgent.
7. Set the Security value to the security model in the OAM Configuration screen of the Identity Management Provisioning Wizard
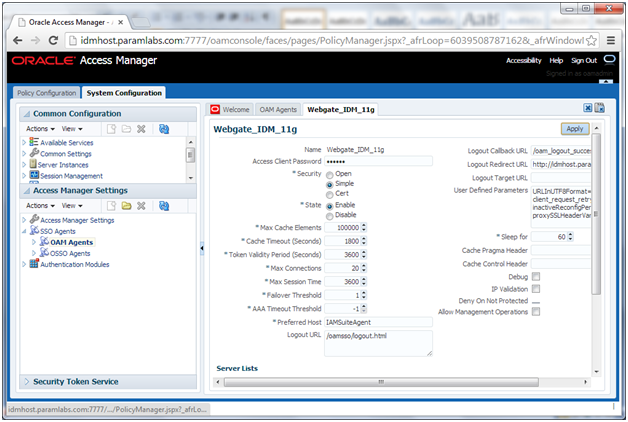
Click Apply.
8. Restart the managed server wls_oam1
Update WebGate Configuration
To update the maximum number of WebGate connections, proceed as follows.
1. In the Oracle Access Manager Console, select the System Configuration tab.
2. Select Access Manager -> SSO Agents -> OAM Agent from the directory tree. Double-click or select the Open Folder icon.
3. On the displayed search page, click Search to perform an empty search.
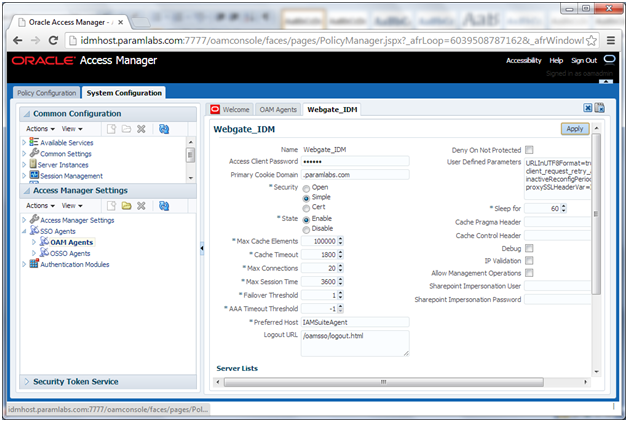
4. Click the Agent Webgate_IDM.
5. Select Open from the Actions menu.
6. Set Maximum Number of Connections to 20
7. Set AAA Timeout Threshold to 5.
8. In the User Defined Parameters box, set client_request_retry_attempts to 11.
9. If the following Logout URLs are not listed, add them:
/oamsso/logout.html
/console/jsp/common/logout.jsp
/em/targetauth/emaslogout.jsp
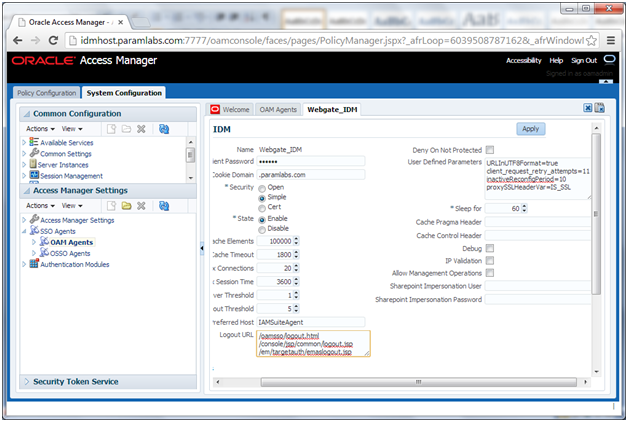
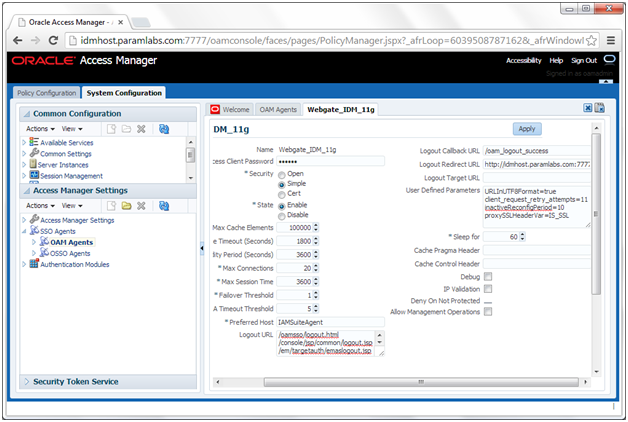
10. Click Apply.
Repeat Steps 4 through 7 for each WebGate
Creating Oracle Access Manager Policies for WebGate 11g
In order to allow WebGate 11g to display the credential collector, you must add /oam to the list of public policies.
Proceed as follows:
1. Log in to the OAM console at: http://idmhost.paramlabs.com:7777/oamconsole
2. Select the Policy Configuration tab.
3. Expand Application Domains – IAM Suite
4. Click Resources.
5. Click Open.
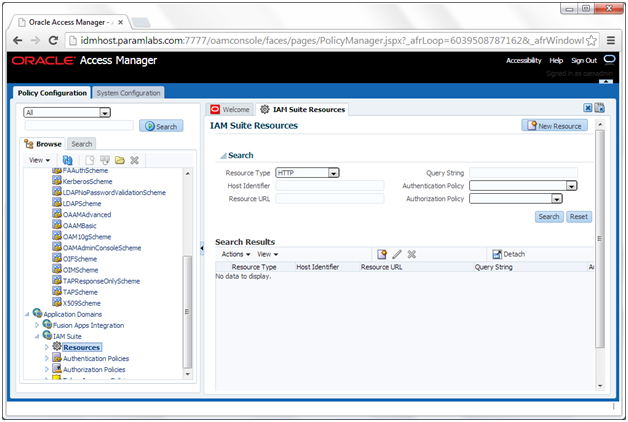
6. Click New resource.
7. Provide the following values:
Type: HTTP
Description: OAM Credential Collector
Host Identifier: IAMSuiteAgent
Resource URL: /oam
Protection Level: Unprotected
Authentication Policy: Public Policy
8. Leave all other fields at their default values.
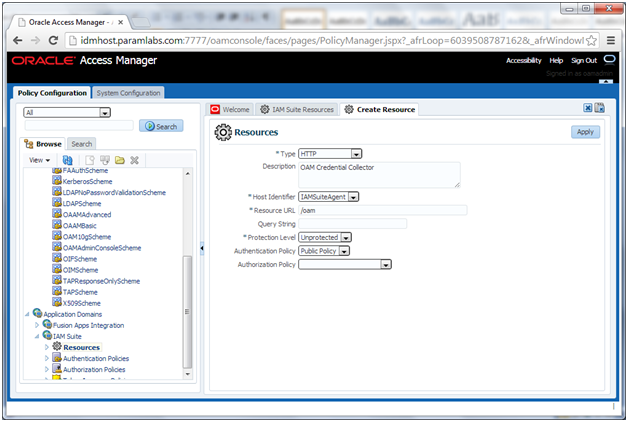
9. Click Apply
Passing Configuration Properties File to Oracle Fusion Applications
[fusion@idmhost ~]$ cd /app/oracle/config/fa/
[fusion@idmhost fa]$ ls -ltr idmsetup.properties
-rw-r–r– 1 fusion dba 3548 Oct 26 02:42 idmsetup.properties
[fusion@idmhost fa]$ cp -pr idmsetup.properties idmsetup.properties.backup
OIF Configuration
OIF is optional and we will skip configuring it
We will also skip “updating node manager for enterprise deployment” since we do not want to configure SSL yet\
Let’s confirm if OID and OHS are running fine.
[fusion@idmhost ~]$ /app/oracle/config/instances/oid1/bin/opmnctl status
Processes in Instance: oid1
———————————+——————–+———+———
ias-component | process-type | pid | status
———————————+——————–+———+———
ovd1 | OVD | 14778 | Alive
oid1 | oidldapd | 15011 | Alive
oid1 | oidldapd | 14999 | Alive
oid1 | oidldapd | 14910 | Alive
oid1 | oidmon | 14780 | Alive
EMAGENT | EMAGENT | 14777 | Alive
[fusion@idmhost ~]$ /app/oracle/config/instances/ohs1/bin/opmnctl status
Processes in Instance: ohs1
———————————+——————–+———+———
ias-component | process-type | pid | status
———————————+——————–+———+———
ohs1 | OHS | 16798 | Alive
Validate OID and OVD
[fusion@idmhost bin]$ ldapbind -h idmhost.paramlabs.com -p 6501 -D “cn=orcladmin” -q
Please enter bind password:
bind successful
[fusion@idmhost bin]$ ldapbind -h idmhost.paramlabs.com -p 7501 -D “cn=orcladmin” -q -U 1
Please enter bind password:
bind successful
[fusion@idmhost bin]$ ldapbind -h idmhost.paramlabs.com -p 3060 -D “cn=orcladmin” -q
Please enter bind password:
bind successful
[fusion@idmhost bin]$ ldapbind -h idmhost.paramlabs.com -p 3131 -D “cn=orcladmin” -q -U 1
Please enter bind password:
bind successful
Validate Admin and managed Servers
Login to Weblogic console at http://idmhost:7777/console using weblogic_idm user. Click on Servers.
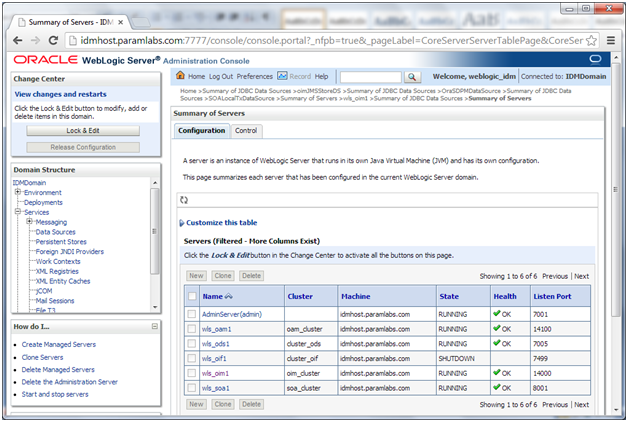
You can see that all servers except OIF are running. This is default configuration after IDM provisioning since OIF is optional and we will not start it.
Login to Enterprise Manager at http://idmhost:7777/em using weblogic_idm user.
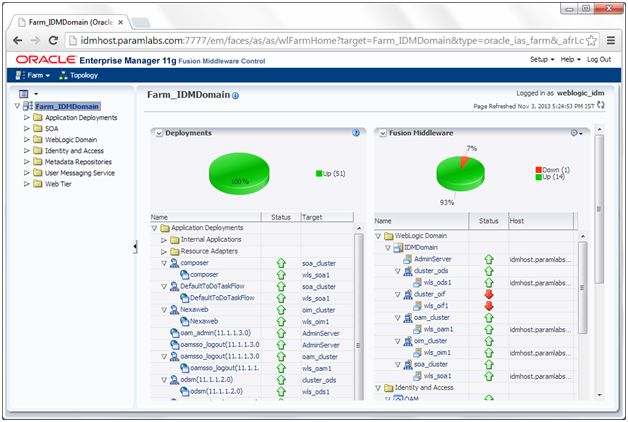
All components except OIF should be green.
Validate OIM by logging into http://idmhost:7777/oim using xelsysadm user
This concludes our IDM host related setup. We will now move on to Fusion Applications host.
Next: Install Fusion Applications Provisioning Framework on FA Host
Installing Oracle Fusion Applications – steps
A. Setting up Identity and Access Management Node
1. Install Fusion Applications Provisioning Framework
2. Install Oracle 11g Database (Identity management database)
3. Run Repository Creation Utility (RCU) for Oracle Identity Management components
4. Install Identity Management Provisioning Wizard
5. Create IDM provisioning Response File
6. Provision Identity Management
7. Perform Post-Provisioning Configuration
B. Setting up Fusion Applications Node
1. Install Fusion Applications Provisioning Framework
2. Install Oracle 11g Database (Fusion Apps Database)
3. Run Oracle Fusion Applications Repository Creation Utility (Applications RCU)
4. Create new Applications Provisioning Response File
5. Provision an Applications Environment






































Recent Comments