Oracle Fusion Applications Installation: Configure Oracle Identity and Access Management components
Previous: Apply mandatory Patches
Configuring Oracle Identity Management components” can be divided into following tasks. Please note that we will not configure Oracle Virtual Directory, Oracle Identity Federation etc.
- Configuring the Web Tier
- Create Weblogic Domain for Identity Management
- Extend the Domain to include Oracle Internet Directory
- Extend the Domain to include Oracle Directory Service Manager (ODSM)
- Prepare Identity and Policy Stores
- Extend the Domain to include Oracle Virtual Directory (Optional)
- Configure Oracle Access Manager 11g (OAM)
- Configure Oracle Identity Manager (OIM) and Oracle SOA Suite
-
Post-configure tasks
Configure Web Tier
Start the configuration from <Web_Home>/bin
-bash-3.2$ cd /app/fusion/fmw/web/bin/
-bash-3.2$ ./config.sh
Click Next
On next page, select only Oracle HTTP Server and deselect other checkboxes. Click Next
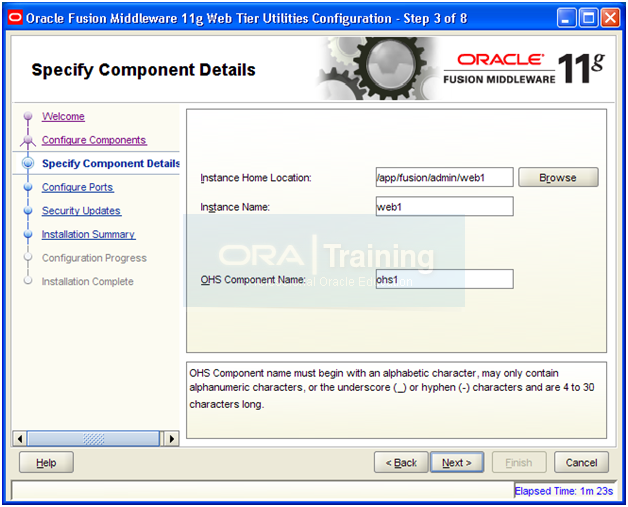
Enter following details and click Next
Instance Home Location: /app/fusion/admin/web1
Instance Name: web1
OHS Component Name: ohs1
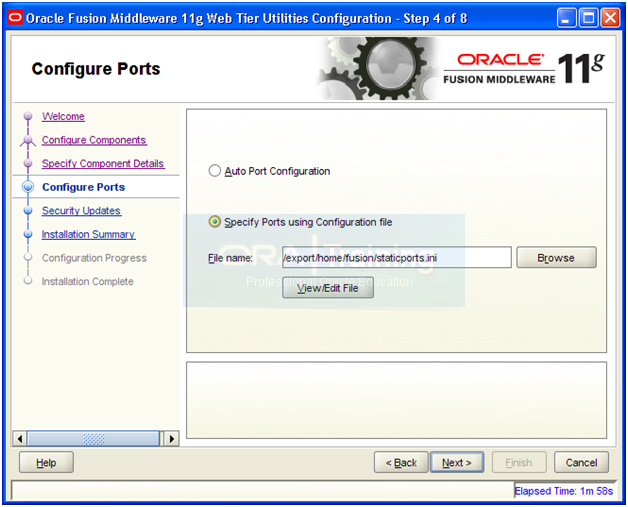
Select “Specify Ports using Configuration file”. Open another shell window and copy the staticports.ini from staging directory.
-bash-3.2$ cp -p /u02/stage/installers/webtier/Disk1/stage/Response/staticports.ini ~/
Click View/Edit File
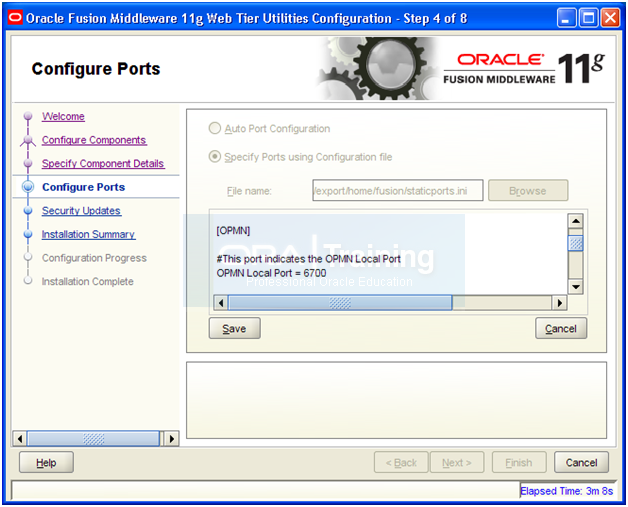
Edit/uncomment the following values.
OPMN Local Port = 6700
OHS Port = 7777
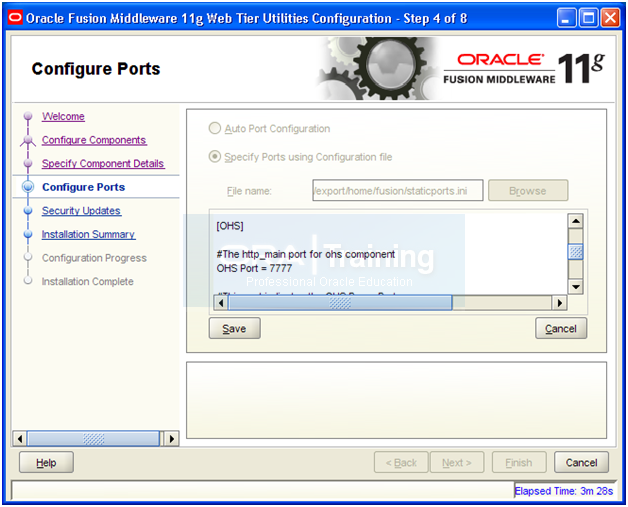
Click Save
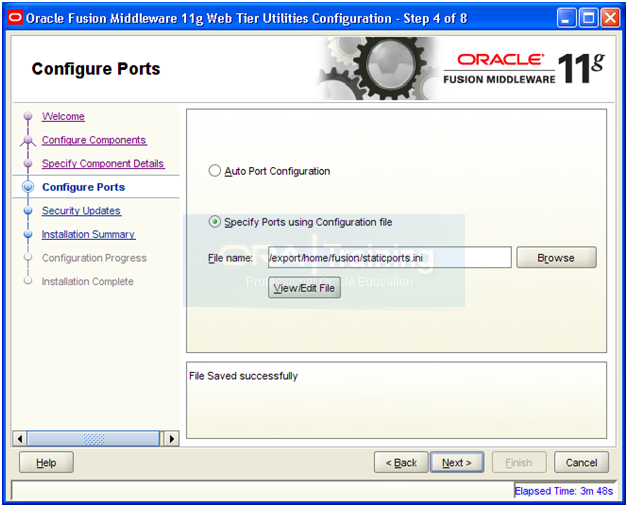
Deselect the check box and click Next
Click Yes
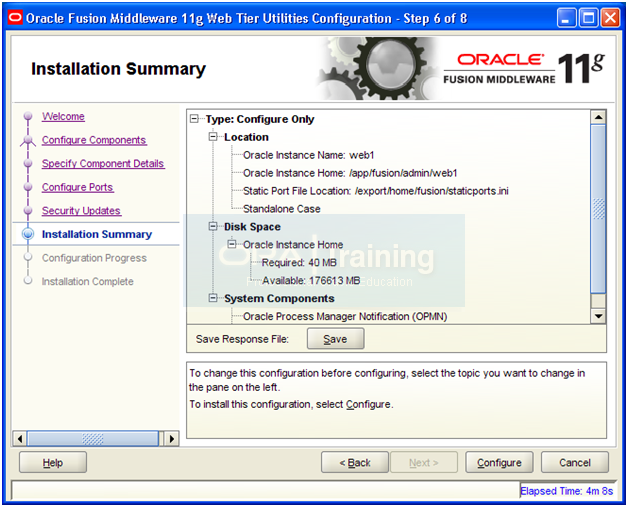
Review the summary and click Configure
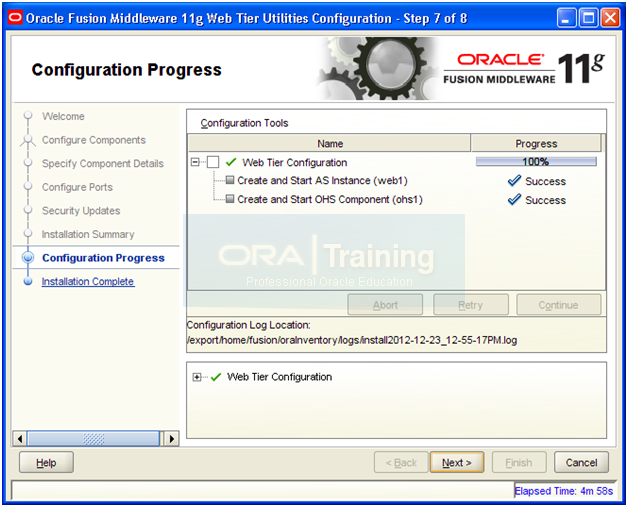
Once installation is successful, click Next
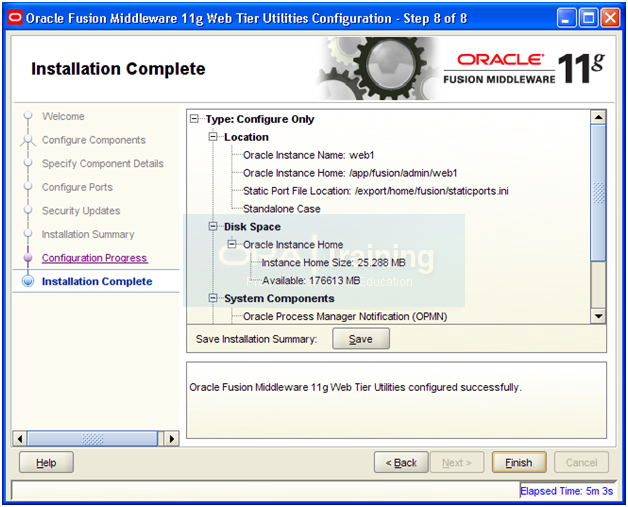
Review the summary and click Finish
-bash-3.2$ ps -ef | grep http
fusion 3568 3558 0 13:00:05 ? 0:00 /app/fusion/fmw/web/ohs/bin/httpd.worker -DSSL
fusion 3558 3553 0 13:00:02 ? 0:01 /app/fusion/fmw/web/ohs/bin/httpd.worker -DSSL
fusion 3567 3558 0 13:00:05 ? 0:00 /app/fusion/fmw/web/ohs/bin/httpd.worker -DSSL
fusion 3566 3558 0 13:00:05 ? 0:00 /app/fusion/fmw/web/ohs/bin/httpd.worker -DSSL
fusion 3584 21657 0 13:00:40 pts/1 0:00 grep http
-bash-3.2$ vi /app/fusion/admin/web1/config/OHS/ohs1/httpd.conf
Change to following (dba or oinstall based on fusion user group)
User fusion
Group dba
Launch http://<hostname>:7777 to make sure that HTTP home page is appearing.
Make a backup of httpd.conf
-bash-3.2$ cp -pr /app/fusion/admin/web1/config/OHS/ohs1/httpd.conf /app/fusion/admin/web1/config/OHS/ohs1/httpd.conf_orig
Modify following values in httpd.conf
-bash-3.2$ vi /app/fusion/admin/web1/config/OHS/ohs1/httpd.conf
…
<IfModule mpm_worker_module>
ServerLimit 20
StartServers 2
MaxClients 1000
MinSpareThreads 200
MaxSpareThreads 800
ThreadsPerChild 50
MaxRequestsPerChild 10000
AcceptMutex fcntl
LockFile “${ORACLE_INSTANCE}/diagnostics/logs/${COMPONENT_TYPE}/${COMPONENT_NAME}/http_lock”
</IfModule>
Create Weblogic Domain for Identity Management
Start the configuration from <Middleware Home>/oracle_common/commin/bin
-bash-3.2$ cd /app/fusion/fmw/oracle_common/common/bin/
-bash-3.2$ ./config.sh &


Select “Create a new Weblogic domain” and click Next
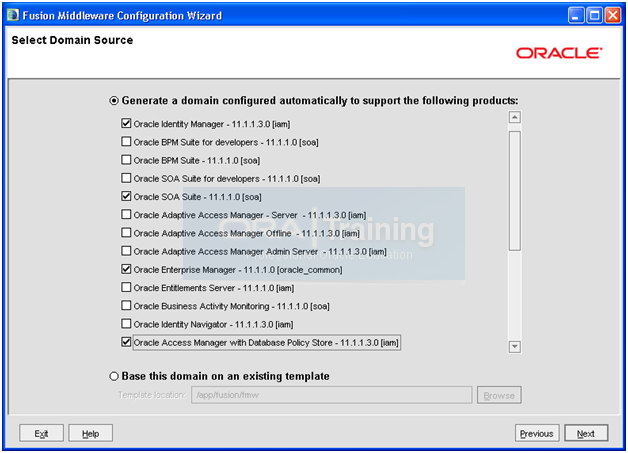
For single domain creation, select:
– Oracle Identity Manager 11.1.1.3.0 [iam]
– Oracle SOA Suite – 11.1.1.0 [soa]
– Oracle Enterprise Manager [oracle_common]
– Oracle Access Manager with Database Policy Store – 11.1.1.3.0 [iam]
– Oracle WSM Policy Manager – 11.1.1.0 [oracle_common]
– Oracle JRF [oracle_common] (This should be selected automatically.)
Click Next
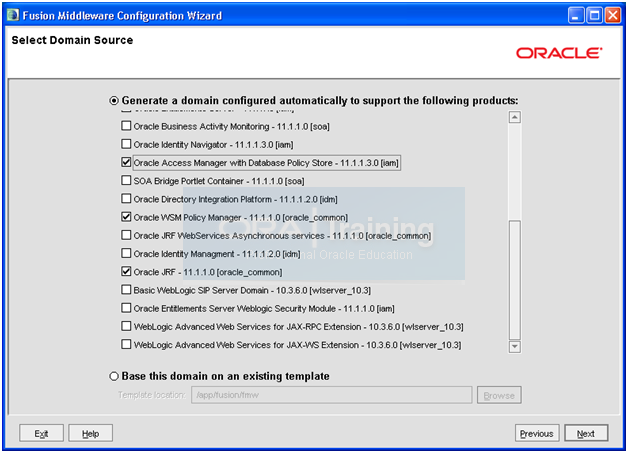
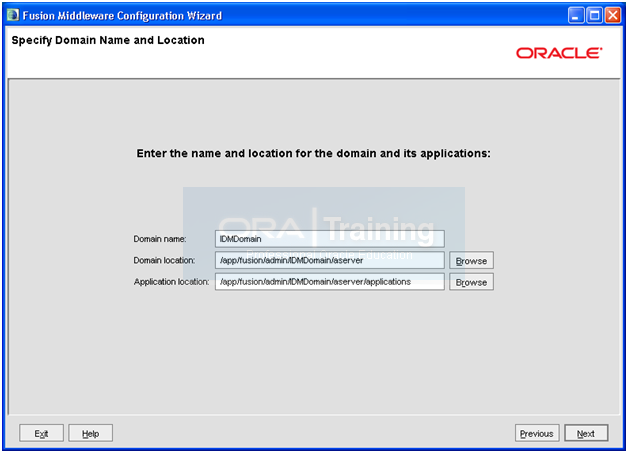
Enter following values.
Domain Name: IDMDomain
Domain location: /app/fusion/admin/IDMDomain/aserver
Application location: Populated automatically
Click Next
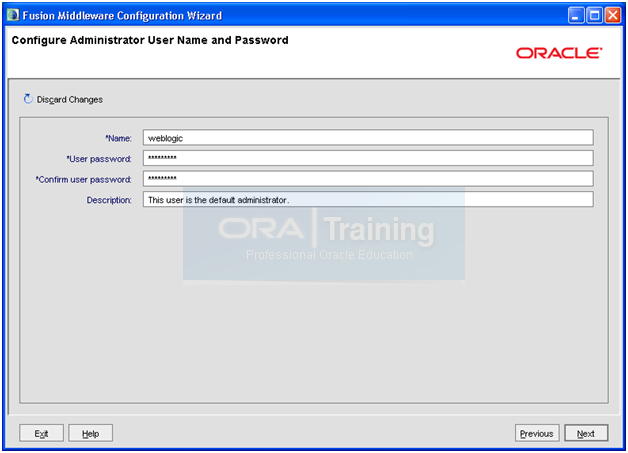
Enter name “weblogic” and desired password. Click Next
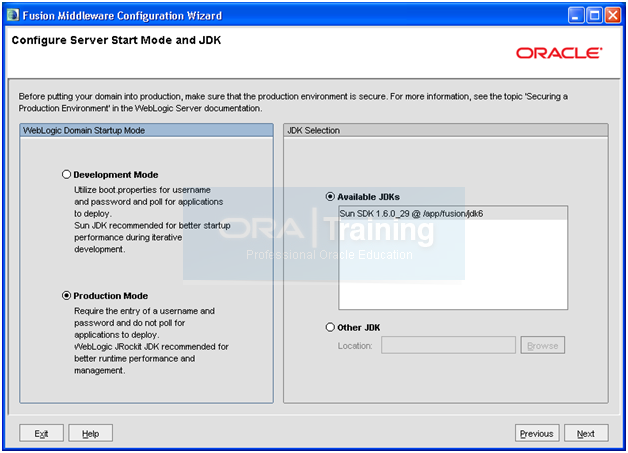
Select “Production Mode” and make sure correct JDK is selected. Click Next
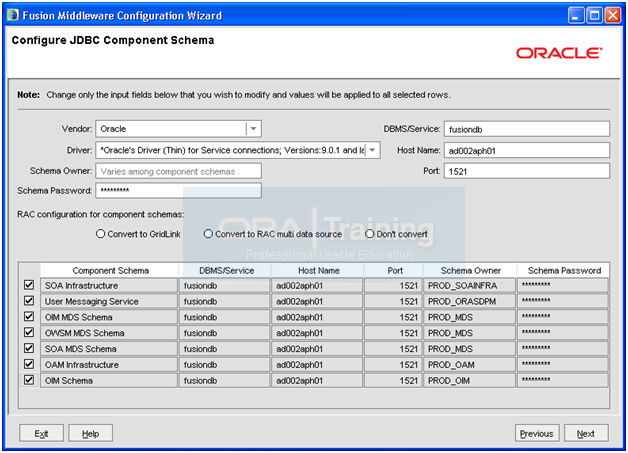
Make sure to change each username to PROD_ since we have modified the prefix earlier. Then select all checkboxes to apply same password. Enter database server details and click Next
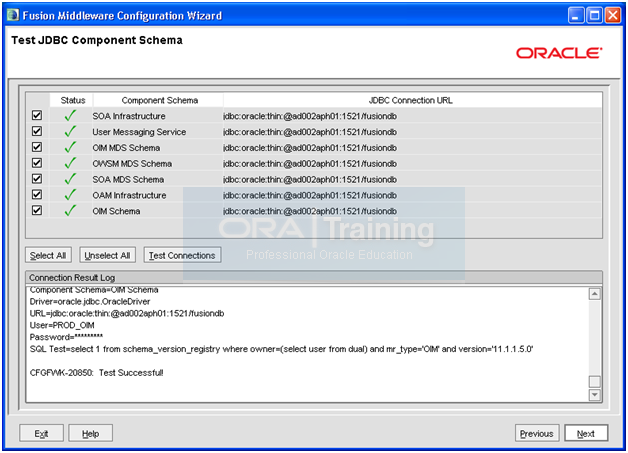
Once connection test is successful, click Next
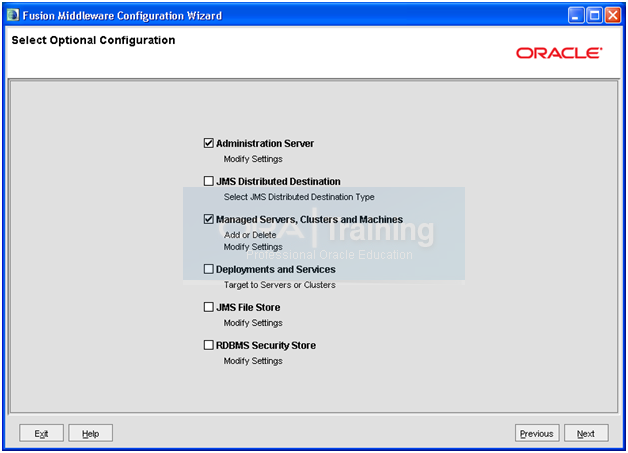
Select “Administration Server” and “Managed servers, clusters and Machines”. Click Next
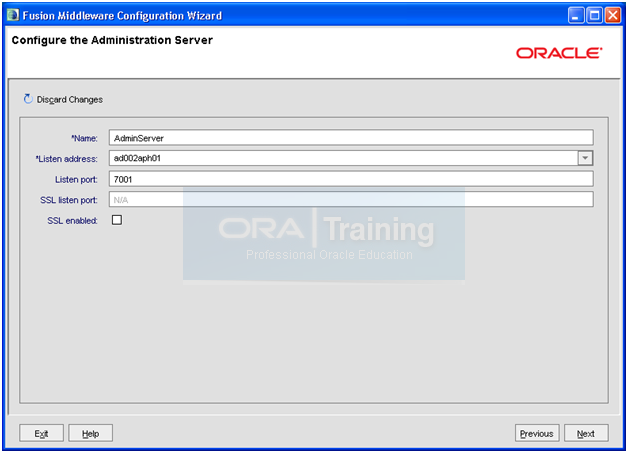
Enter following values.
Name: AdminServer
Listen address: <hostname>
Listen Port: <7001>
We are not using SSL here so click Next
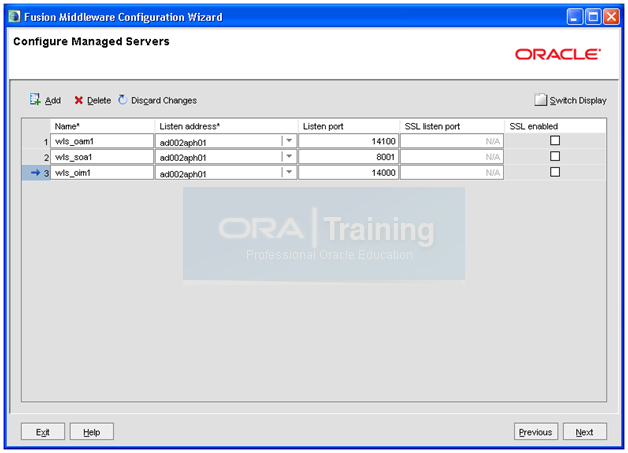
In the “Configure Managed Servers” screen enter following values.
wls_oam1 , <hostname>, 14100 (OAM Server)
wls_soa1, <hostname>, 8001 (SOA Server)
wls_oim1, <hostname>, 14000 (OIM Server)
Click Next
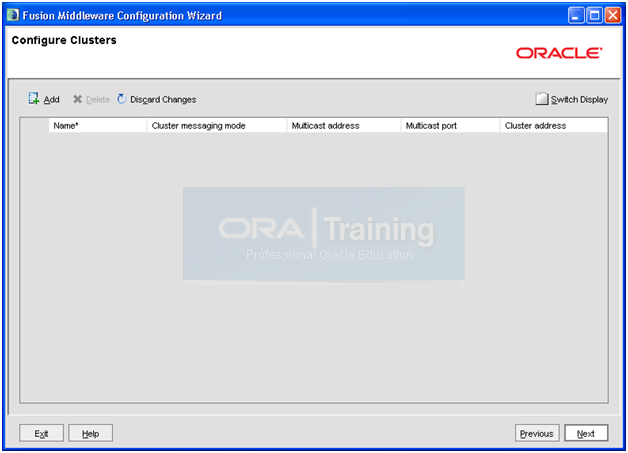
Click Next
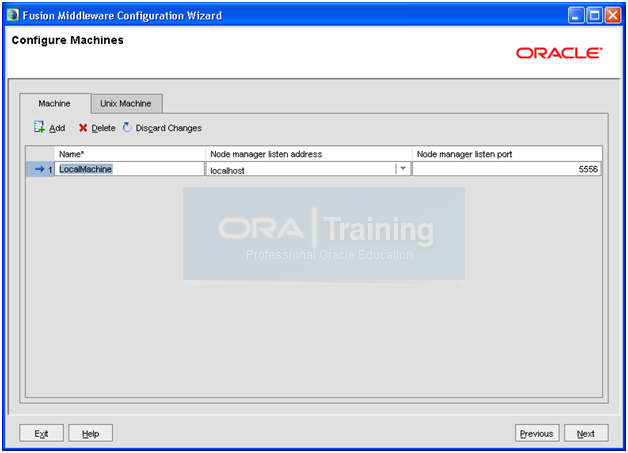
Since we are using Unix machine, we must delete this entry. Click Delete
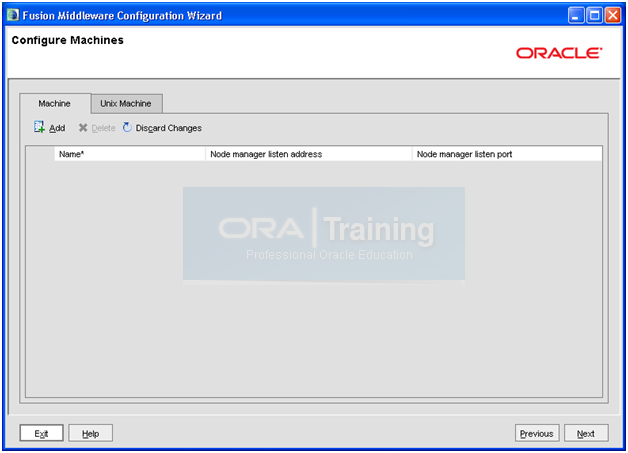
This tab should look like this.
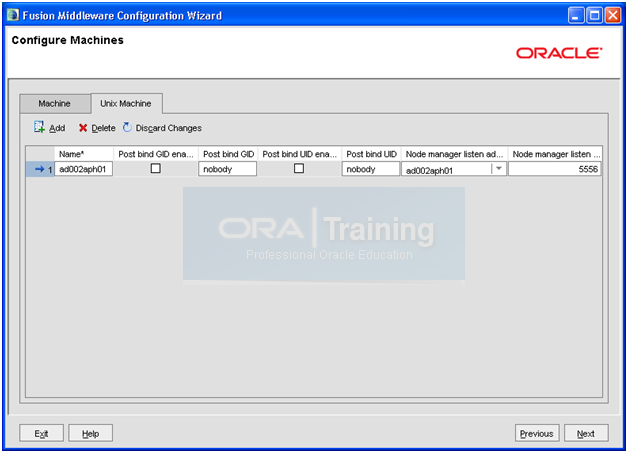
Click on “Unix Machine” tab and enter following values. And click Next
Name: <hostname>
Node Manager listen address: <hostname>
Node manager listen port: 5556
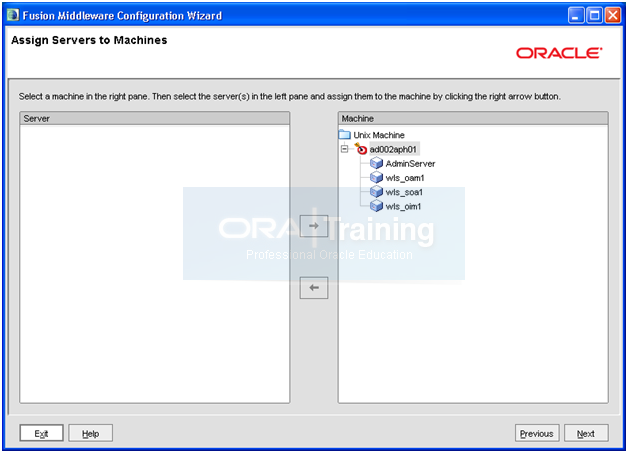
Select all managed servers on left side and click on right arrow to assign all servers to our single node. Click Next
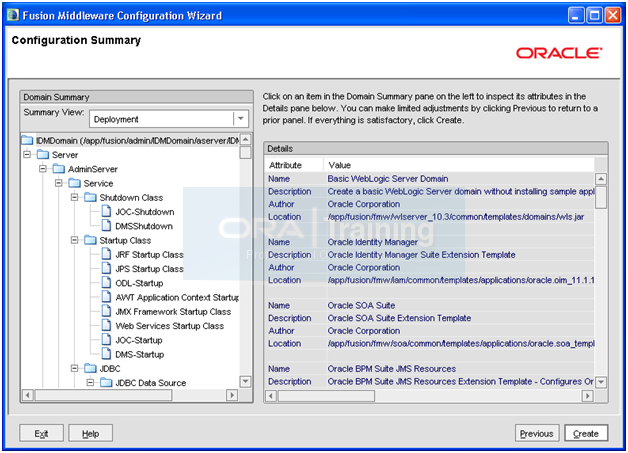
Review the summary and click “Create”
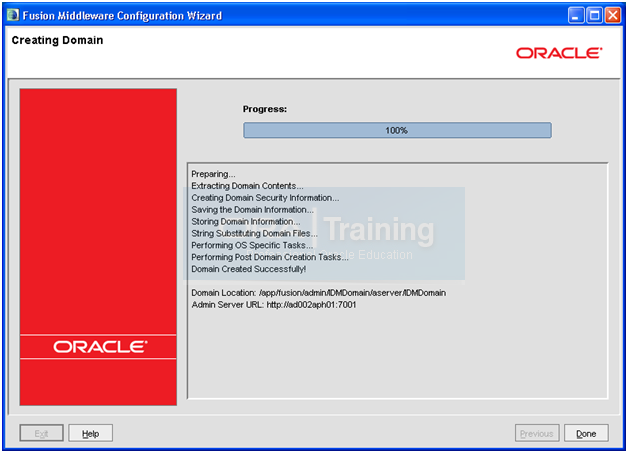
Once creation is complete, click Done
Prepare Admin server for startup without prompting password
-bash-3.2$ mkdir -p /app/fusion/admin/IDMDomain/aserver/IDMDomain/servers/AdminServer/security
-bash-3.2$
cd /app/fusion/admin/IDMDomain/aserver/IDMDomain/servers/AdminServer/security-bash-3.2$ vi boot.properties
Enter following values and save the file
username=weblogic
password=Oracle123 (or whichever password you chose)
Note: The username and password entries in the file are not encrypted until you start the Administration Server. For security reasons, minimize the time the entries in the file are left unencrypted. After you edit the file, start the server as soon as possible so that the entries are encrypted.
Configure and start Node Manager
-bash-3.2$ cd /app/fusion/fmw/wlserver_10.3/server/bin/
-bash-3.2$ ./startNodeManager.sh &
…
INFO: Secure socket listener started on port 5556
Once you see the above message, node manager is able to start correctly.
Kill the node manager process.
-bash-3.2$ ps -ef | grep Node
fusion 5563 21657 0 13:32:01 pts/1 0:00 grep Node
fusion 5511 21657 0 13:31:31 pts/1 0:00 /bin/sh ./startNodeManager.sh
-bash-3.2$ kill -9 5511
Set the node manager properties
-bash-3.2$ cd /app/fusion/fmw/oracle_common/common/bin
-bash-3.2$ ./setNMProps.sh
Appending required nodemanager.properties
To confirm the changes,
-bash-3.2$ tail -f /app/fusion/fmw/wlserver_10.3/common/nodemanager/nodemanager.properties
…
…
#Required NM Property overrides (append to existing nodemanager.properties)
StartScriptEnabled=true
Start node manager in nohup mode so that it keeps running after you close the shell.
-bash-3.2$ cd /app/fusion/fmw/wlserver_10.3/server/bin/
-bash-3.2$ nohup ./startNodeManager.sh &
Start Weblogic Admin server
-bash-3.2$ cd /app/fusion/admin/IDMDomain/aserver/IDMDomain/bin
-bash-3.2$ nohup ./startWebLogic.sh &
-bash-3.2$ tail -f nohup.out
Wait till you see this message.
…
<Notice> <WebLogicServer> <BEA-000360> <Server started in RUNNING mode>
==========
Note: If you ever get error like
<Info> <Management> <BEA-141281> <unable to get file lock, will retry …>
Then do the following
Kill any running processes for startWeblogic.sh and then remove the lock files as follows.
-bash-3.2$ rm /app/fusion/admin/IDMDomain/aserver/IDMDomain/servers/AdminServer/tmp/AdminServer.lok
This error appears if you the admin server or managed server did not stop properly earlier.
==========
Make sure Admin server is started properly by launching the URL http://<hostname>:7001/console
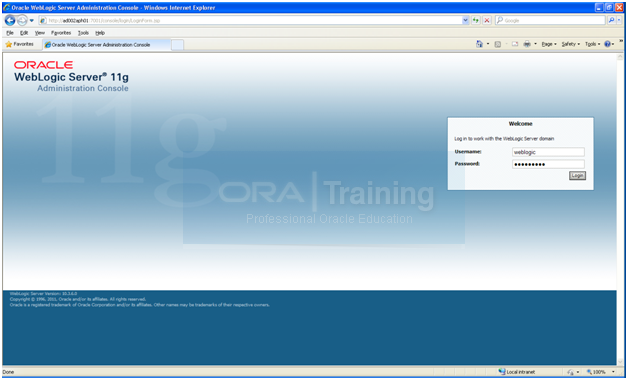
Login with “weblogic” user.
Launch Enterprise Manager URL
Login with weblogic user
Setup Aliases
Create a file named admin.conf at <web instance directory>/config/OHS/ohs1/moduleconf and enter following lines
-bash-3.2$ more /app/fusion/admin/web1/config/OHS/ohs1/moduleconf/admin.conf
# Admin Server and EM
<Location /console>
SetHandler weblogic-handler
WebLogicHost ad002aph01
WeblogicPort 7001
</Location>
<Location /consolehelp>
SetHandler weblogic-handler
WebLogicHost ad002aph01
WeblogicPort 7001
</Location>
<Location /em>
SetHandler weblogic-handler
WebLogicHost ad002aph01
WeblogicPort 7001
</Location>
Restart Web server
-bash-3.2$ /app/fusion/admin/web1/bin/opmnctl stopall
opmnctl stopall: stopping opmn and all managed processes…
-bash-3.2$ /app/fusion/admin/web1/bin/opmnctl startall
opmnctl startall: starting opmn and all managed processes…
Now you can launch the same URL using our main http port 7777
http://<hostname>:7777/console should open fine now
Register HTTP server with Enterprise Manager
-bash-3.2$ cd /app/fusion/admin/web1/bin/
-bash-3.2$ ./opmnctl registerinstance -adminHost ad002aph01 -adminport 7001 -adminUsername weblogic
Command requires login to weblogic admin server (ad002aph01):
Username: weblogic
Password:
…
Done
Registering instance
Command succeeded.
Creating a Separate Domain Directory for Managed Servers in the Same Node as the Administration Server
-bash-3.2$ mkdir /app/fusion/admin/IDMDomain/mserver
-bash-3.2$ cd /app/fusion/fmw/oracle_common/common/bin/-bash-3.2$ ./pack.sh -managed=true -domain=/app/fusion/admin/IDMDomain/aserver/IDMDomain -template=domaintemplate.jar -template_name=domain_template
============
<< read domain from “/app/fusion/admin/IDMDomain/aserver/IDMDomain”
>> succeed: read domain from “/app/fusion/admin/IDMDomain/aserver/IDMDomain”
<< set config option Managed to “true”
>> succeed: set config option Managed to “true”
<< write template to “/app/fusion/fmw/oracle_common/common/bin/domaintemplate.jar”
……………………………………………………………………………………….
>> succeed: write template to “/app/fusion/fmw/oracle_common/common/bin/domaintemplate.jar”
<< close template
>> succeed: close template
============
-bash-3.2$ ./unpack.sh -domain=/app/fusion/admin/IDMDomain/mserver/IDMDomain -template=domaintemplate.jar -app_dir=/app/fusion/admin/IDMDomain/mserver/applications
=============
<< read template from “/app/fusion/fmw/oracle_common/common/bin/domaintemplate.jar”
>> succeed: read template from “/app/fusion/fmw/oracle_common/common/bin/domaintemplate.jar”
<< set config option AppDir to “/app/fusion/admin/IDMDomain/mserver/applications”
>> succeed: set config option AppDir to “/app/fusion/admin/IDMDomain/mserver/applications”
<< set config option DomainName to “IDMDomain”
>> succeed: set config option DomainName to “IDMDomain”
<< write Domain to “/app/fusion/admin/IDMDomain/mserver/IDMDomain”
>> warning:write Domain to “/app/fusion/admin/IDMDomain/mserver/IDMDomain”
>> Server listen ports in your domain configuration conflict with ports in use by active processes on this host.
Port 7001 on AdminServer
…………………………………………………………………………………..
>> succeed: write Domain to “/app/fusion/admin/IDMDomain/mserver/IDMDomain”
<< close template
>> succeed: close template
============
Copy SOA Composites to Managed Server Directory
-bash-3.2$ cp -pr /app/fusion/admin/IDMDomain/aserver/IDMDomain/soa /app/fusion/admin/IDMDomain/mserver/IDMDomain/
Enable Weblogic Plugin
Open http://<hostname>:7777/console and login with weblogic user
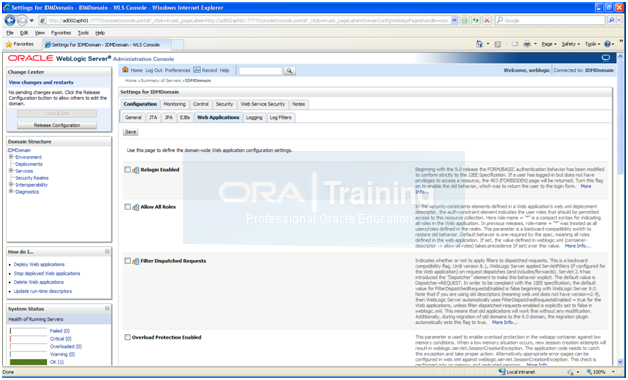
Click Lock & Edit. Click on IDMDomain -> Configuration -> Web Applications
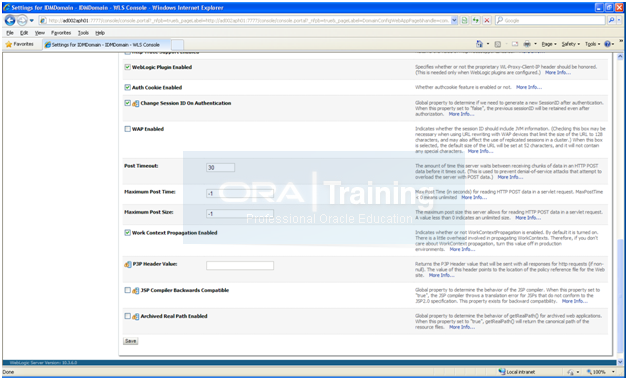
Scroll down and check “Weblogic Plugin Enabled”
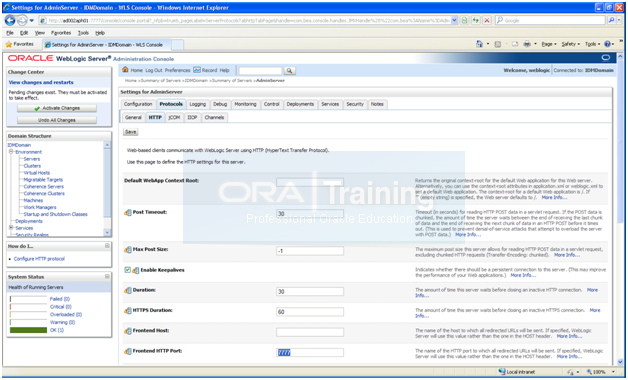
Click on Environment -> Servers -> AdminServer -> Protocols -> HTTP. Change the Frontend port to 7777. Activate Changes
Removing IDM Domain Agent
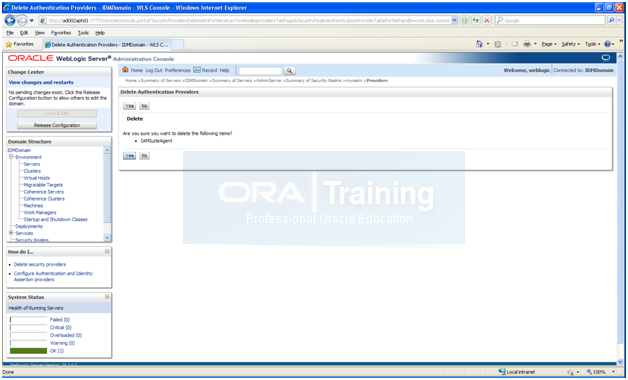
In the Administration console, click on “Security Realms” -> myrealm -> Providers
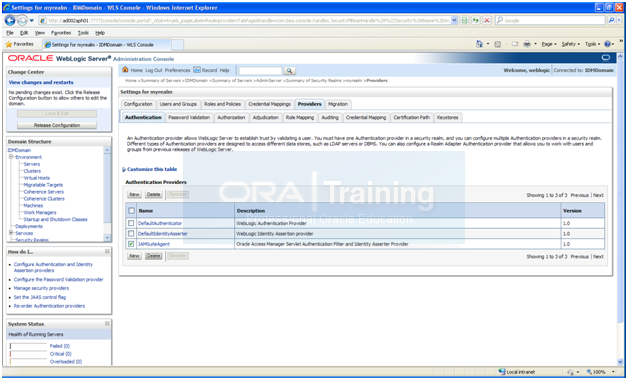
Select IAMSuiteAgent and click on Delete. Activate Changes
Restart AdminServer
Extend the Domain to include Oracle Internet Directory
Make sure that the port 3060 is not being used by other process.
-bash-3.2$ netstat -an | grep “3060”
Start the configuration from <IDM_HOME>/bin
-bash-3.2$ cd /app/fusion/fmw/idm/bin
-bash-3.2$ ./config.sh &
Click Next
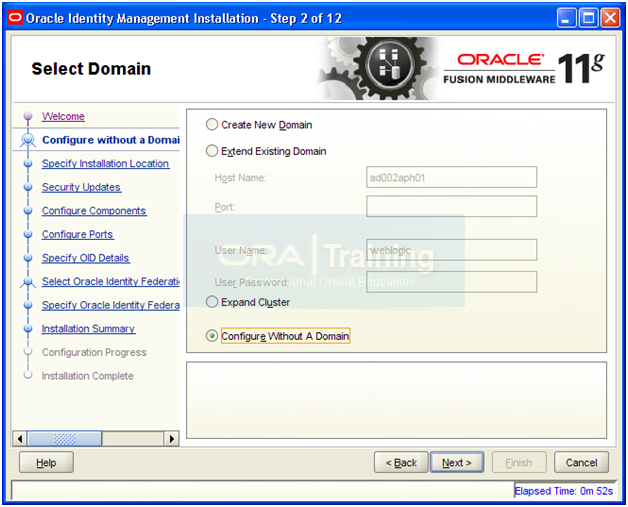
Select “Configure Without A Domain” and click Next
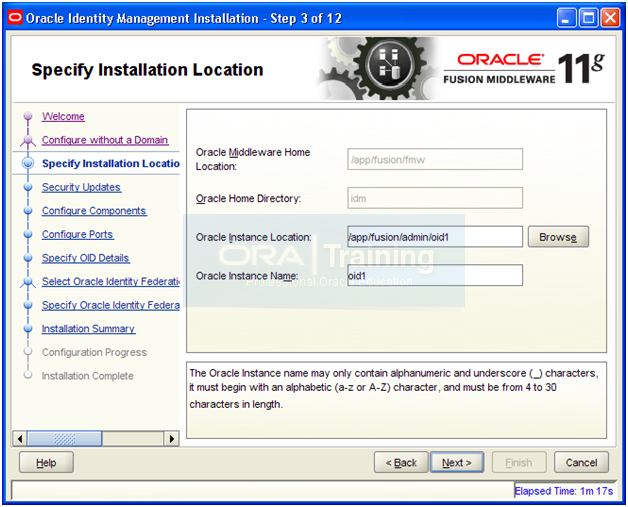
Instance Location: /app/fusion/admin/oid1
Instance Name: oid1
Click Next
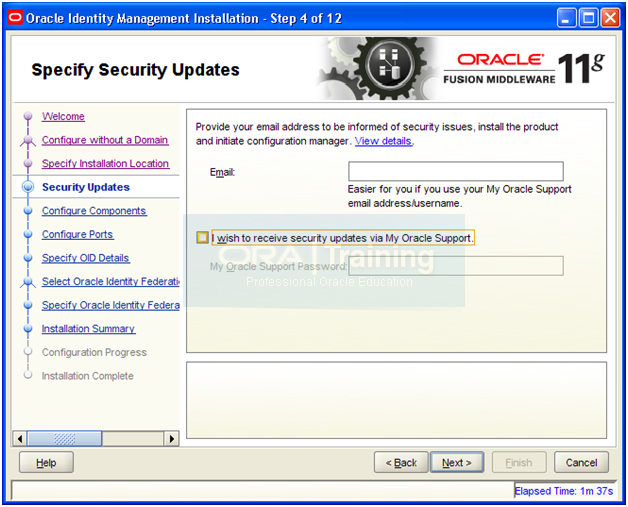
Deselect checkbox and click Next
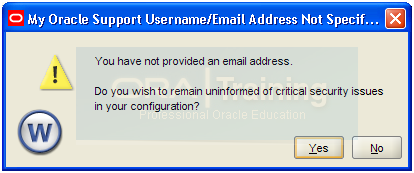
Click Yes
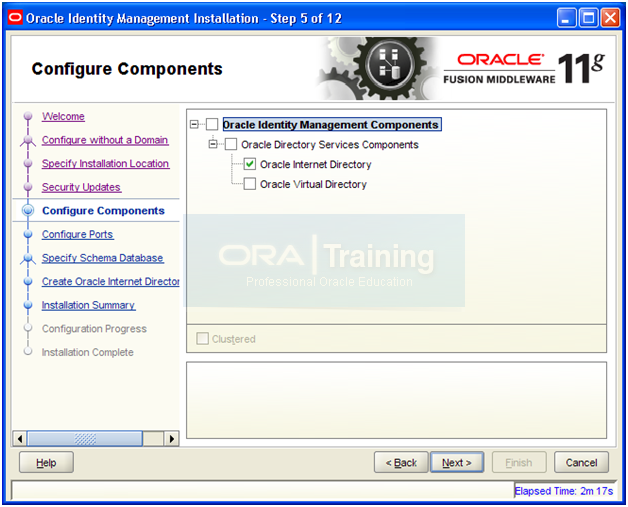
Select “Oracle Internet Directory” and click Next
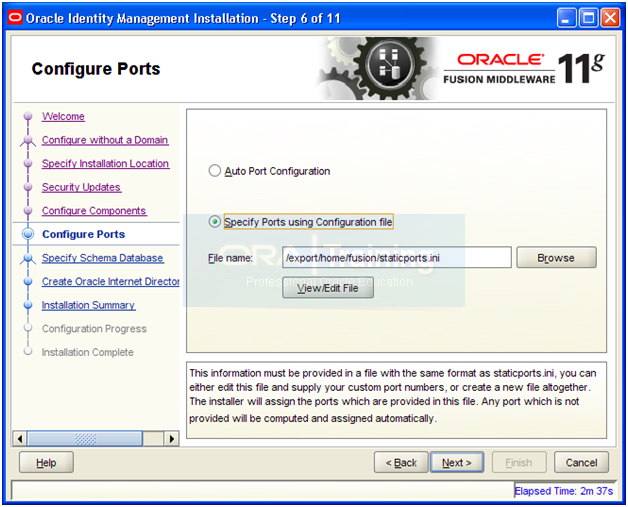
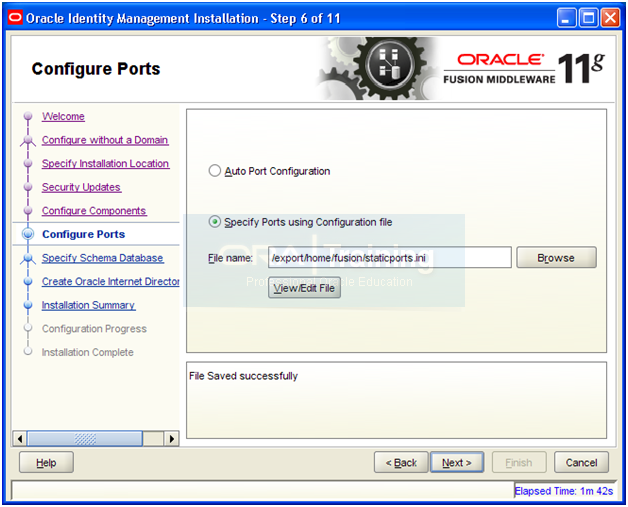
Select “Specify Ports using Configuration file”
Open a shell and copy the staticports.ini file to home directory
-bash-3.2$ cp -p /app/fusion/provisioning/idm/Disk1/stage/Response/staticports.ini ~/
Click View/Edit File
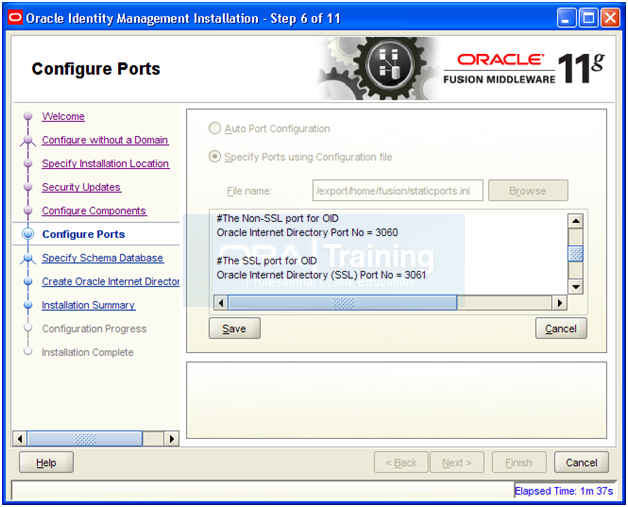
Enter/uncomment Value for Non-SSL Port as 3060
And for SSL Port put value as 3061
Click Save
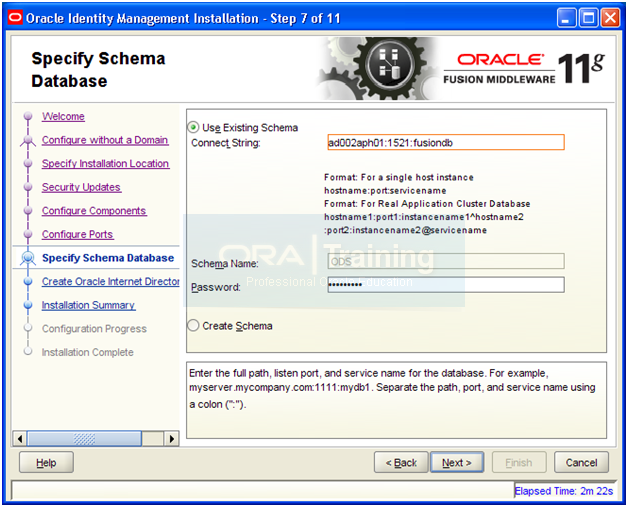
Enter database details and click Next
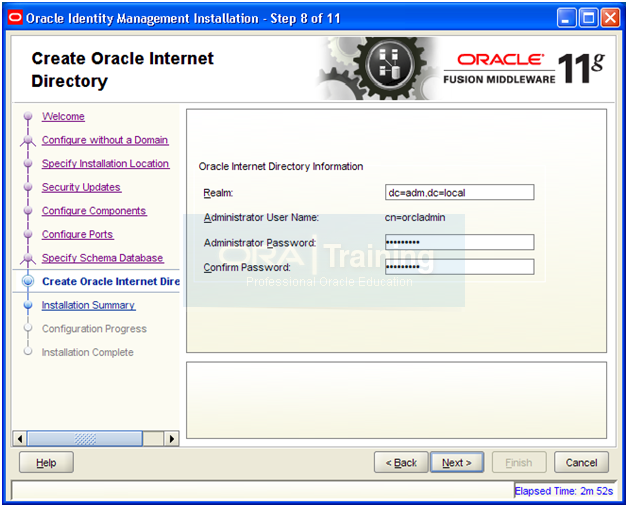
Set Realm as the domain level DC (for example if domain is example.com then set dc=example, dc=com)
Click Next
Review the summary and click Configure
Once configuration completes, click Next
Review the summary and click Finish
Validate OID
-bash-3.2$ export ORACLE_HOME=/app/fusion/fmw/idm
-bash-3.2$ export ORACLE_INSTANCE=/app/fusion/admin/oid1
-bash-3.2$ export PATH=$ORACLE_HOME/opmn/bin:$ORACLE_HOME/bin:$ORACLE_HOME/ldap/bin:$ORACLE_HOME/ldap/admin:$PATH
-bash-3.2$ ldapbind -h ad002aph01 -p 3060 -D “cn=orcladmin” -q
Please enter bind password:
bind successful
-bash-3.2$ ldapbind -h ad002aph01 -p 3061 -D “cn=orcladmin” -q -U 1
Please enter bind password:
bind successful
-bash-3.2$ opmnctl status
Processes in Instance: oid1
———————————+——————–+———+———
ias-component | process-type | pid | status
———————————+——————–+———+———
oid1 | oidldapd | 8499 | Alive
oid1 | oidldapd | 8495 | Alive
oid1 | oidmon | 8491 | Alive
EMAGENT | EMAGENT | 8266 | Alive
Registering Oracle Internet Directory with the WebLogic Server Domain
-bash-3.2$ export ORACLE_HOME=/app/fusion/fmw/idm
-bash-3.2$ export ORACLE_INSTANCE=/app/fusion/admin/oid1
-bash-3.2$ $ORACLE_INSTANCE/bin/opmnctl registerinstance -adminHost ad002aph01 -adminPort 7001 -adminUsername weblogic
Command requires login to weblogic admin server (ad002aph01):
Username: weblogic
Password:
Registering instance
Command succeeded.
Update the Enterprise Manager Repository URL
-bash-3.2$ cd $ORACLE_INSTANCE/EMAGENT/EMAGENT/bin
-bash-3.2$ ./emctl switchOMS http://<hostname>:7001/em/upload
Oracle Enterprise Manager 10g Release 5 Grid Control 10.2.0.5.0.
Copyright (c) 1996, 2009 Oracle Corporation. All rights reserved.
SwitchOMS succeeded.
We can now verify whether this instance is registered for monitoring agent.
Login to http://<hostname>:7777/em using weblogic user
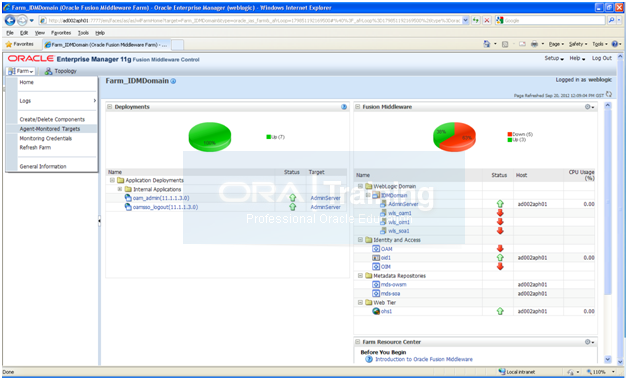
Click on Farm->Agent monitored targets.
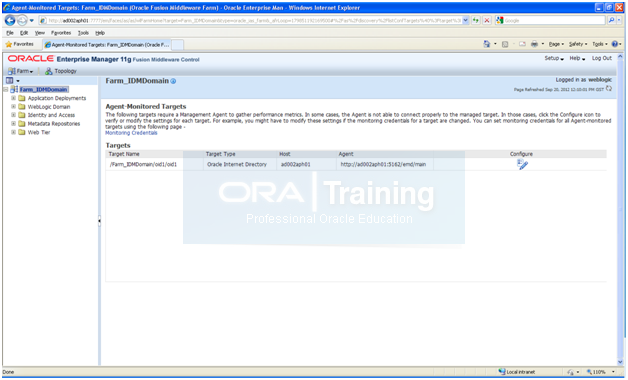
Make sure that Agent URL is configured and it does not show “Needs Configuration”
Note: We will not tune OID but it is recommended to do this on production systems.
Extend the Domain to include Oracle Directory Service Manager (ODSM)
Make sure that the port 7006 is not being used by any process.
-bash-3.2$ netstat -an | grep “7006”
Start the configuration from <IDM_HOME>/bin
-bash-3.2$ cd /app/fusion/fmw/idm/bin/
-bash-3.2$ ./config.sh &

Click Next
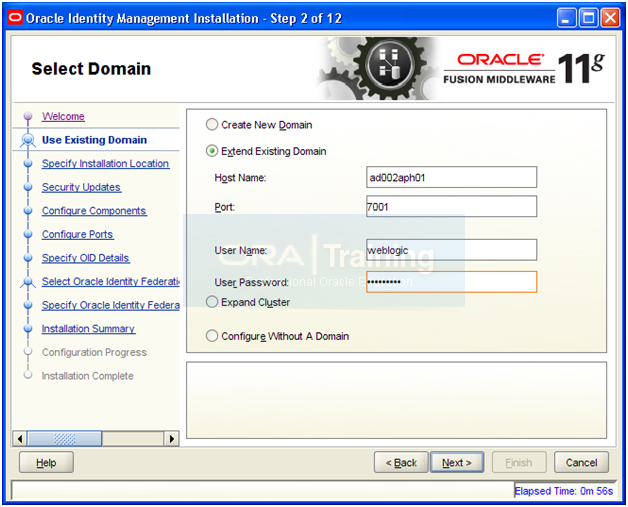
Select “Extend Existing Domain” and enter following values
Hostname: <hostname>
Port: 7001
Username: weblogic
Password: same as existing weblogic password
Click Next
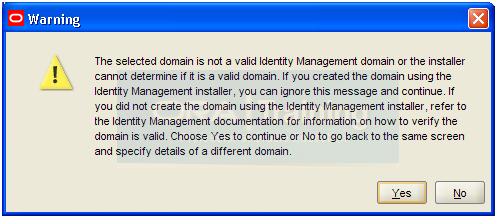
Click Yes
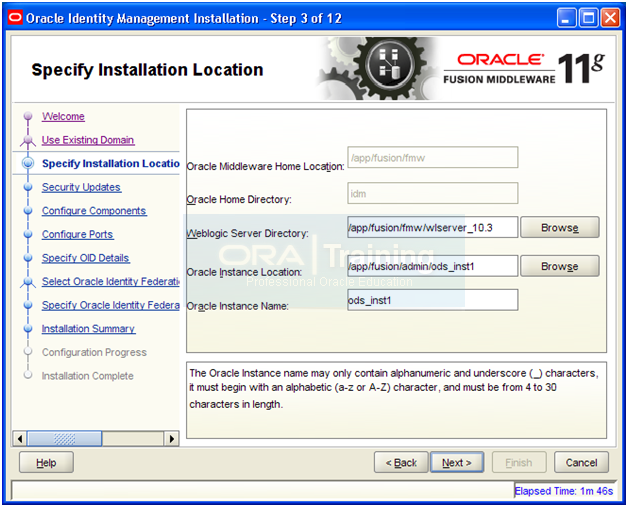
Enter following values.
Weblogic Server Directory: /app/fusion/fmw/wlserver_10.3
Instance location: /app/fusion/admin/ods_inst1
Instance Name: ods_inst1
Click Next
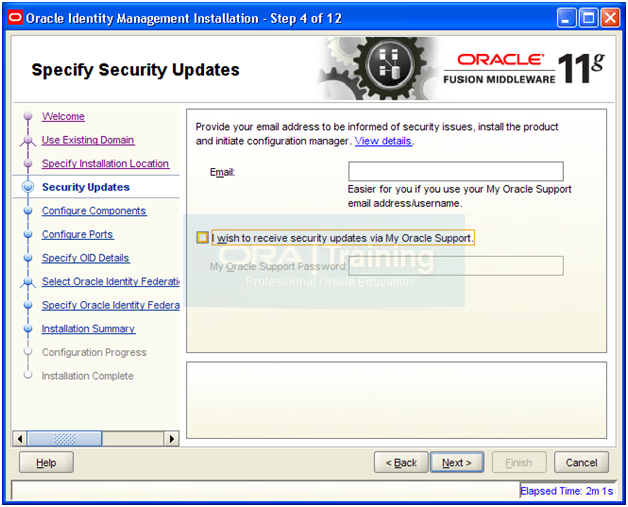
Deselect checkbox and click Next
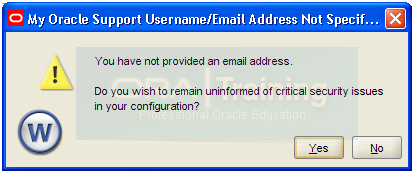
Click Yes
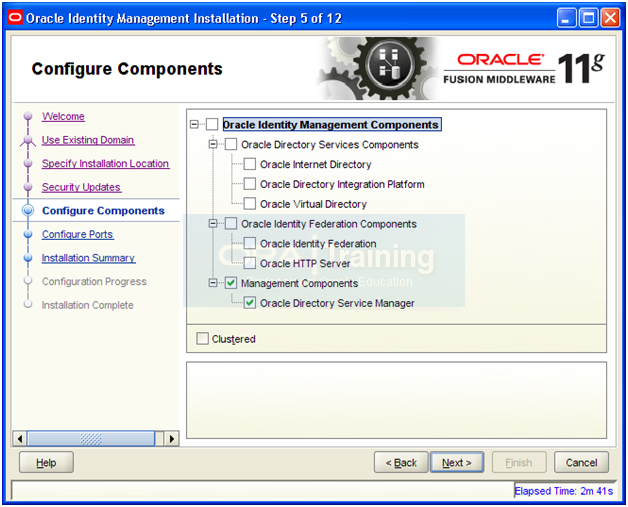
Select only Oracle Directory Service Manager and click Next
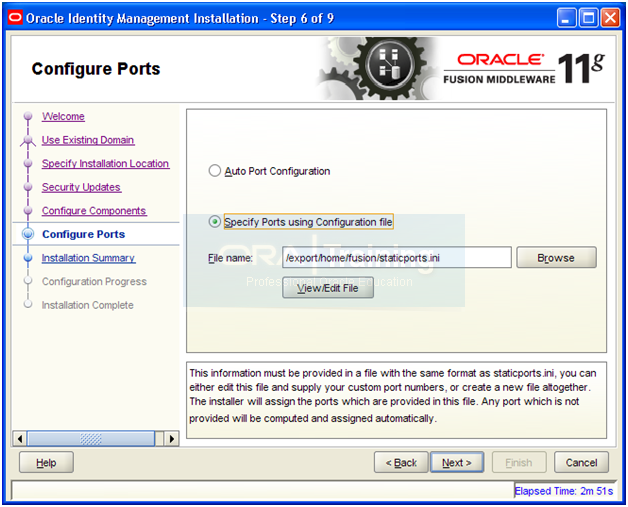
Select “Specify Ports using Configuration file”. Open another shell window and copy the staticports.ini from staging directory.
-bash-3.2$ cp -p /app/fusion/provisioning/idm/Disk1/stage/Response/staticports.ini ~/
Click View/Edit File
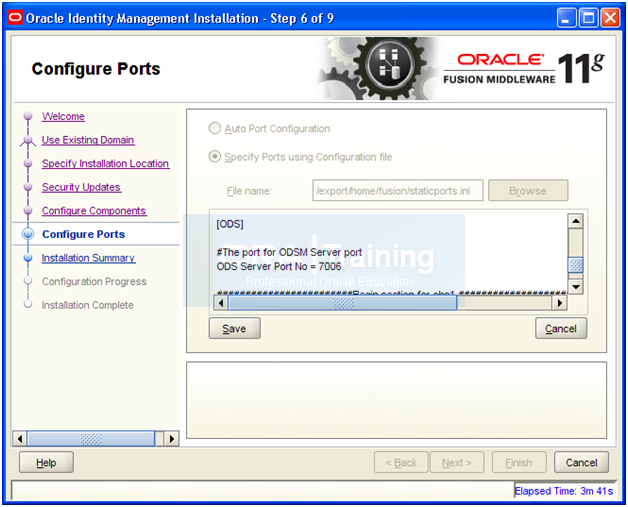
Edit/uncomment ODS server Port No = 7006
Click Save
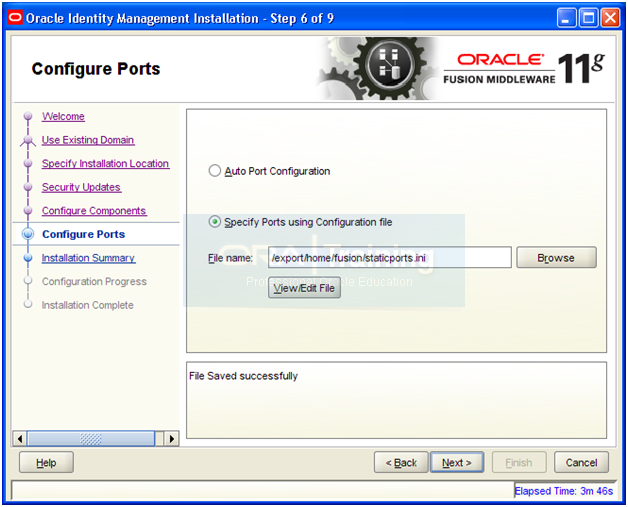
Review the summary and click Configure
Once configuration completes, click Next
Review the summary and click Finish
Check if wls_ods1 is already up in Enterprise Manager at http://<hostname>:7777/em
If not up the start by following commands.
-bash-3.2$ cd /app/fusion/admin/IDMDomain/aserver/IDMDomain/servers/wls_ods1/security/
-bash-3.2$ cp ../../AdminServer/security/boot.properties .
-bash-3.2$ cd /app/fusion/admin/IDMDomain/aserver/IDMDomain/bin/
-bash-3.2$ nohup ./startManagedWebLogic.sh wls_ods1 &
Wait till you see RUNNING in the nohup.log file
Launch ODSM using following URL
Create Aliases for ODSM in HTTP server
-bash-3.2$ cd /app/fusion/admin/ohs_inst1/config/OHS/ohs1/moduleconf/
Append following entries in admin.conf file
-bash-3.2$ vi admin.conf
Append
<Location /odsm>
SetHandler weblogic-handler
WebLogicHost ad002aph01
WeblogicPort 7006
</Location>
Restart Web Server
-bash-3.2$ /app/fusion/admin/ohs_inst1/bin/opmnctl stopall
opmnctl stopall: stopping opmn and all managed processes…
-bash-3.2$ /app/fusion/admin/ohs_inst1/bin/opmnctl startall
opmnctl startall: starting opmn and all managed processes…
Now you can also launch ODSM using following URL
Click on Connect to a directory ->
Create A New Connection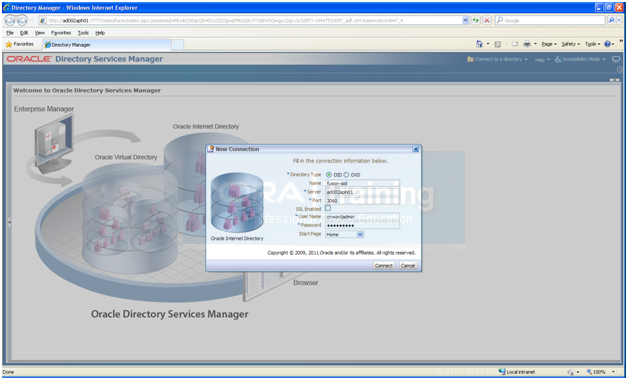
Enter values as follows.
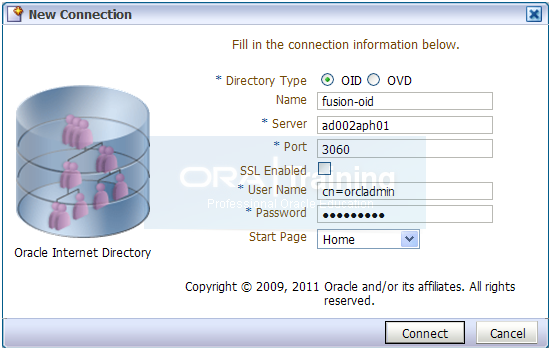
Click Connect
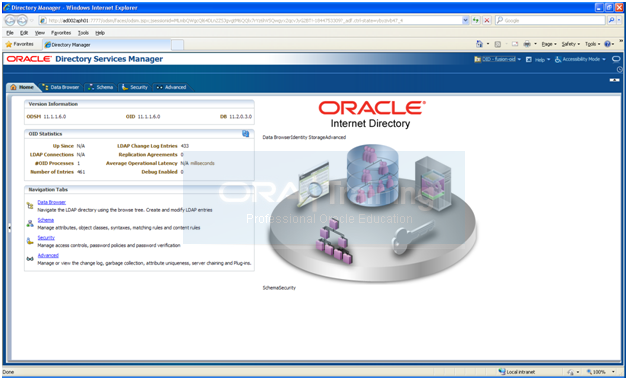
You can now view the Oracle Internet Directory from ODSM
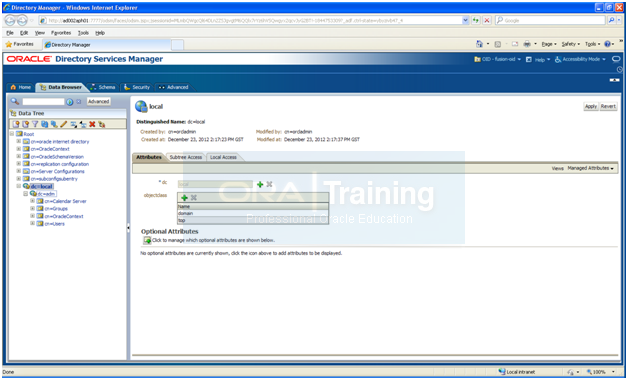
You can also browse the OID data as above
Provisioning the Managed Servers in the Managed Server Directory
Stop the ODS
Use pack and unpack commands to provision the managed servers in mserver directory
-bash-3.2$ cd /app/fusion/fmw/oracle_common/common/bin/
-bash-3.2$ ./pack.sh -managed=true -domain=/app/fusion/admin/IDMDomain/aserver/IDMDomain -template=/app/fusion/fmw/templates/managedServer.jar -template_name=ManagedServer_Template
-bash-3.2$ ./unpack.sh -domain=/app/fusion/admin/IDMDomain/mserver/IDMDomain -template=/app/fusion/fmw/templates/managedServer.jar -app_dir=/app/fusion/admin/IDMDomain/mserver/applications -overwrite_domain=true
Make sure to use the switch –overwrite_domain=true
Start wls_ods1
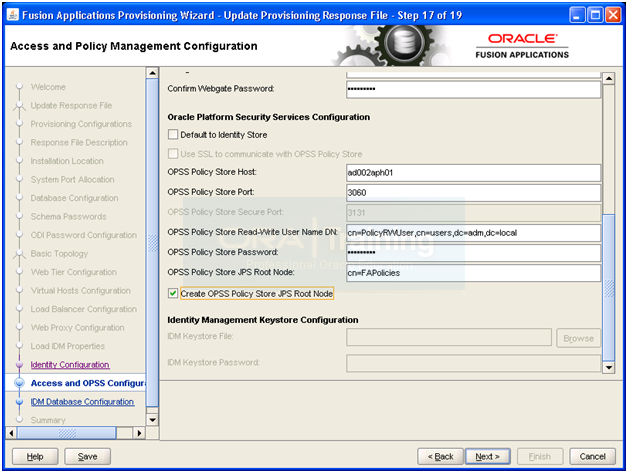
Prepare Identity and Policy Stores
Prepare Policy store
Go to directory <IAM_HOME>/idmtools/bin
-bash-3.2$ cd /app/fusion/fmw/iam/idmtools/bin/
Source environment variables
-bash-3.2$ export ORACLE_HOME=/app/fusion/fmw/iam
-bash-3.2$ export JAVA_HOME=/app/fusion/jdk6
-bash-3.2$ export IDM_HOME=/app/fusion/fmw/idm
-bash-3.2$ export MW_HOME=/app/fusion/fmw
Create a file named policystore.props
-bash-3.2$ more policystore.props
POLICYSTORE_HOST: ad002aph01
POLICYSTORE_PORT: 3060
POLICYSTORE_BINDDN: cn=orcladmin
POLICYSTORE_READONLYUSER: PolicyROUser
POLICYSTORE_READWRITEUSER: PolicyRWUser
POLICYSTORE_SEARCHBASE: dc=adm,dc=local
POLICYSTORE_CONTAINER: cn=jpsroot
Run the following command.
-bash-3.2$ ./idmConfigTool.sh -configPolicyStore input_file=policystore.props
Enter Policy Store Bind DN password :
…
Enter User Password for PolicyROUser:
Confirm User Password for PolicyROUser:
…
Enter User Password for PolicyRWUser:
Confirm User Password for PolicyRWUser:
-bash-3.2$ grep -i error automation.log
Note: While running this command, you might see the following error message:
WARNING: Error in adding in-memory OID search filters.
You may safely ignore this error.
Run following commands to reassociate Security Store
-bash-3.2$ cd /app/fusion/fmw/oracle_common/common/bin/
-bash-3.2$ ./wlst.sh
wls:/offline> connect(“weblogic”,”Oracle123″,”t3://<hostname>:7001″)
wls:/IDMDomain/serverConfig> reassociateSecurityStore(domain=”IDMDomain”, admin=”cn=orcladmin”,password=”Oracle123″, ldapurl=”ldap://<hostname>:3060″,servertype=”OID”, jpsroot=”cn=jpsroot”)
…
wls:/IDMDomain/serverConfig> exit()
Restart Admin Server
Prepare Identity Store
Go to <IAM_HOME>/idmtools/bin
-bash-3.2$ cd /app/fusion/fmw/iam/idmtools/bin/
Create a file named idstore.props
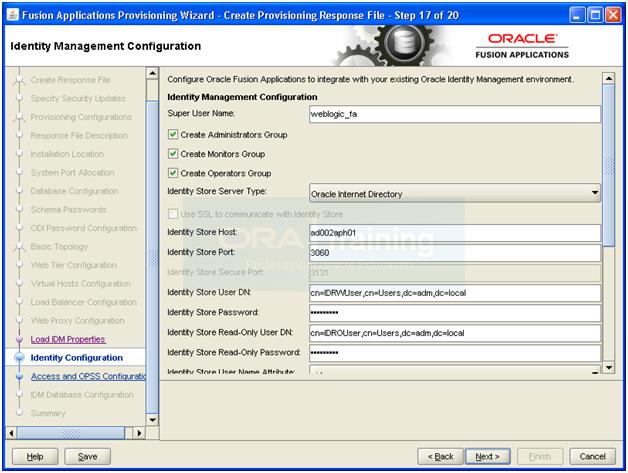
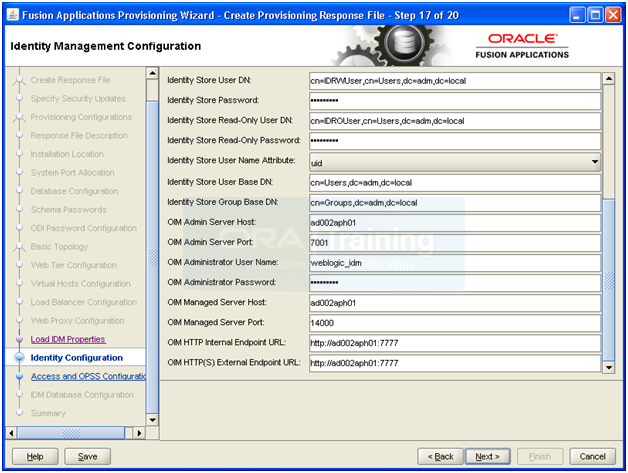
-bash-3.2$ more idstore.props
# Common
IDSTORE_HOST: ad002aph01
IDSTORE_PORT: 3060
IDSTORE_BINDDN: cn=orcladmin
IDSTORE_GROUPSEARCHBASE: cn=Groups,dc=adm,dc=local
IDSTORE_SEARCHBASE: dc=adm,dc=local
IDSTORE_USERNAMEATTRIBUTE: cn
IDSTORE_LOGINATTRIBUTE: uid
IDSTORE_USERSEARCHBASE: cn=Users,dc=adm,dc=local
POLICYSTORE_SHARES_IDSTORE: true
# OAM
IDSTORE_OAMADMINUSER:oamadmin
IDSTORE_OAMSOFTWAREUSER:oamLDAP
OAM11G_IDSTORE_ROLE_SECURITY_ADMIN:OAMAdministrators
# OAM and OIM
IDSTORE_SYSTEMIDBASE: cn=systemids,dc=adm,dc=local
# OIM
IDSTORE_OIMADMINGROUP: OIMAdministrators
IDSTORE_OIMADMINUSER: oimLDAP
# Required due to bug
IDSTORE_OAAMADMINUSER : oaamadmin
# Fusion Applications
IDSTORE_READONLYUSER: IDROUser
IDSTORE_READWRITEUSER: IDRWUser
IDSTORE_SUPERUSER: weblogic_fa
# Weblogic
IDSTORE_WLSADMINUSER : weblogic_idm
Run following command
-bash-3.2$ ./idmConfigTool.sh -preConfigIDStore input_file=idstore.props
Enter ID Store Bind DN password :
Make sure automation.log is created
-bash-3.2$ ls -l automation.log
-rw-r–r– 1 fusion dba 3432 Sep 20 13:49 automation.log
Check the log for errors
-bash-3.2$ grep -i error automation.log
Note: You might see a warning messages similar to this in the log.
WARNING: Error indexing displayName
You may safely ignore this error.
The above commands will create a file named idmDomainConfig.param file. This is an important file and we will seed the values from this file to the response file.
-bash-3.2$ more idmDomainConfig.param (Generated automatically)
IDSTORE_GROUPSEARCHBASE: cn=Groups,dc=adm,dc=local
POLICYSTORE_PORT: 3060
IDSTORE_HOST: ad002aph01
IDSTORE_LOGINATTRIBUTE: uid
IDSTORE_PORT: 3060
POLICYSTORE_CONTAINER: cn=jpsroot
IDSTORE_USERSEARCHBASE: cn=Users,dc=adm,dc=local
POLICYSTORE_HOST: ad002aph01
POLICYSTORE_READWRITE_USERNAME: cn=PolicyRWUser,cn=users,dc=adm,dc=local
Creating Users and Groups
Run following command.
-bash-3.2$ ./idmConfigTool.sh -prepareIDStore mode=all input_file=idstore.props
Enter ID Store Bind DN password :
…
Enter User Password for IDROUser:
Confirm User Password for IDROUser:
…
Enter User Password for IDRWUser:
Confirm User Password for IDRWUser:
…
Enter User Password for weblogic_fa:
Confirm User Password for weblogic_fa:
…
Enter User Password for weblogic_idm:
Confirm User Password for weblogic_idm:
…
Enter User Password for oblixanonymous:
Confirm User Password for oblixanonymous:
…
Enter User Password for oamadmin:
Confirm User Password for oamadmin:
…
Enter User Password for oamLDAP:
Confirm User Password for oamLDAP:
…
Enter User Password for oaamadmin:
Confirm User Password for oaamadmin:
…
Enter User Password for oimLDAP:
Confirm User Password for oimLDAP:
…
Enter User Password for xelsysadm:
Confirm User Password for xelsysadm:
The tool has completed its operation. Details have been logged to automation.log
-bash-3.2$ grep -i error automation.log
Note: We are not using Oracle Virtual Directory (OVD) since this is optional component so skipping OVD part
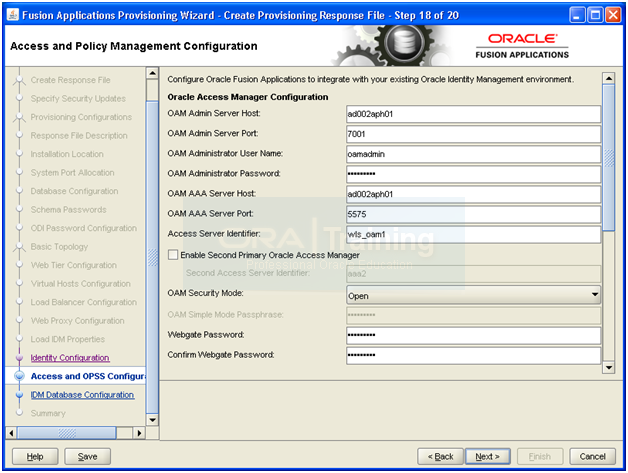
Configure Oracle Access Manager 11g (OAM)
Start managed server wls_oam1 from Administration console.
Configure Aliases for OAM in HTTP server
Append following in /app/fusion/admin/ohs_inst1/config/OHS/ohs1/moduleconf/admin.conf
<Location /oam>
SetHandler weblogic-handler
WebLogicHost ad002aph01
WebLogicPort 14100
</Location>
<Location /fusion_apps>
SetHandler weblogic-handler
WebLogicHost ad002aph01
WebLogicPort 14100
</Location>
<Location /oamconsole>
SetHandler weblogic-handler
WebLogicHost ad002aph01
WebLogicPort 7001
</Location>
Restart Web server
-bash-3.2$ /app/fusion/admin/ohs_inst1/bin/opmnctl stopall
opmnctl stopall: stopping opmn and all managed processes…
-bash-3.2$ /app/fusion/admin/ohs_inst1/bin/opmnctl startall
opmnctl startall: starting opmn and all managed processes…
Now you can launch OAM Console with following URL
http://<hostname>:7777/oamconsole
Login with weblogic user
Configure OAM
Go to <IAM_HOME>/idmtools/bin
-bash-3.2$ cd /app/fusion/fmw/iam/idmtools/bin
Create a file named config_oam1.props
-bash-3.2$ more config_oam1.props
WLSHOST: ad002aph01
WLSPORT: 7001
WLSADMIN: weblogic
WLSPASSWD: Oracle123
IDSTORE_HOST: ad002aph01
IDSTORE_PORT: 3060
IDSTORE_DIRECTORYTYPE:OID
IDSTORE_BINDDN: cn=orcladmin
IDSTORE_USERNAMEATTRIBUTE: cn
IDSTORE_LOGINATTRIBUTE: uid
IDSTORE_USERSEARCHBASE: cn=Users,dc=adm,dc=local
IDSTORE_SEARCHBASE: dc=adm,dc=local
IDSTORE_GROUPSEARCHBASE: cn=Groups,dc=adm,dc=local
IDSTORE_OAMSOFTWAREUSER: oamLDAP
IDSTORE_OAMADMINUSER: oamadmin
PRIMARY_OAM_SERVERS: ad002aph01:5575
WEBGATE_TYPE: ohsWebgate11g
ACCESS_GATE_ID: Webgate_IDM
OAM11G_IDM_DOMAIN_OHS_HOST:ad002aph01
OAM11G_IDM_DOMAIN_OHS_PORT:7777
OAM11G_IDM_DOMAIN_OHS_PROTOCOL:http
OAM11G_WG_DENY_ON_NOT_PROTECTED: false
OAM_TRANSFER_MODE: open
OAM11G_OAM_SERVER_TRANSFER_MODE:open
OAM11G_IDM_DOMAIN_LOGOUT_URLS:/console/jsp/common/logout.jsp,/em/targetauth/emaslogout.jsp
OAM11G_OIM_WEBGATE_PASSWD: Oracle123
COOKIE_DOMAIN: .adm.local
OAM11G_IDSTORE_ROLE_SECURITY_ADMIN: OAMAdministrators
OAM11G_SSO_ONLY_FLAG: true
OAM11G_OIM_INTEGRATION_REQ: true
OAM11G_IMPERSONATION_FLAG:true
OAM11G_SERVER_LBR_HOST:ad002aph01
OAM11G_SERVER_LBR_PORT:7777
OAM11G_SERVER_LBR_PROTOCOL:http
COOKIE_EXPIRY_INTERVAL: 120
OAM11G_OIM_OHS_URL:http://ad002aph01:7777/
OAM11G_SERVER_LOGIN_ATTRIBUTE: uid
Keep a backup of idmDomainConfig.param for safety
-bash-3.2$ cp -pr idmDomainConfig.param idmDomainConfig.param.preOAM
Run the following command to Configure OAM
-bash-3.2$ ./idmConfigTool.sh -configOAM input_file=config_oam1.props
Enter ID Store Bind DN password :
Enter User Password for IDSTORE_PWD_OAMSOFTWAREUSER:
Confirm User Password for IDSTORE_PWD_OAMSOFTWAREUSER:
Enter User Password for IDSTORE_PWD_OAMADMINUSER:
Confirm User Password for IDSTORE_PWD_OAMADMINUSER:
The tool has completed its operation. Details have been logged to automation.log
-bash-3.2$ grep -i error automation.log
WARNING: Error in adding in-memory OID search filters
WARNING: Error indexing displayName
Backup important files generated
-bash-3.2$ cp -pr /app/fusion/admin/IDMDomain/aserver/IDMDomain/output/Webgate_IDM/ ~/backup/
Restart ALL managed servers and Admin server
Validate OAM
Login to OAM Console using oamadmin user
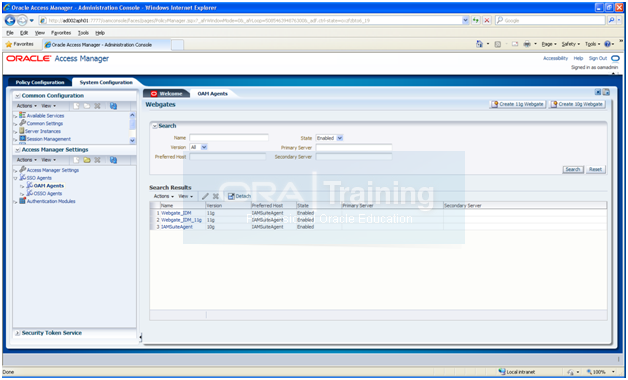
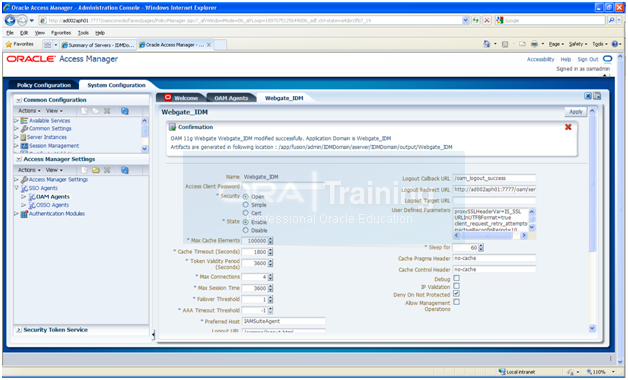
In System Configuration tab, click Access Manager Settings -> SSO Agents-> OAM Agents. Search for all agents.
Edit Webgate_IDM agent
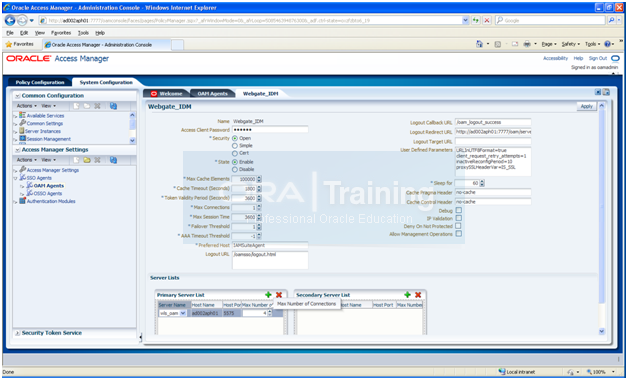
Set Max. number of Connections to 4 for each primary servers (in our case only one host is there)
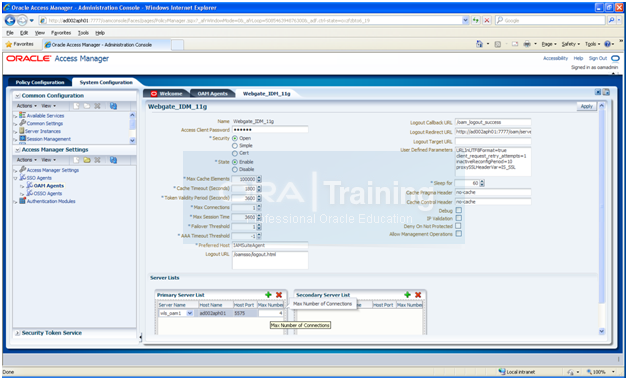
Do the same for Webgate_IDM_11g agent
Set Max. number of Connections to 4 for each primary servers (in our case only one host is there)
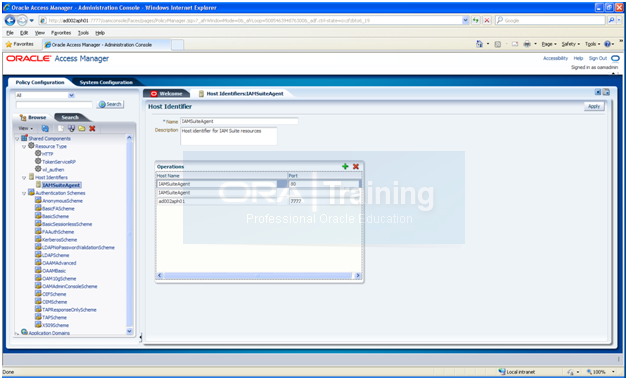
In Policy Configurations tab, Host identifiers->IAMSuiteAgent-> Make sure our hostname and the default http port is mentioned. If already there then nothing to change in this screen.
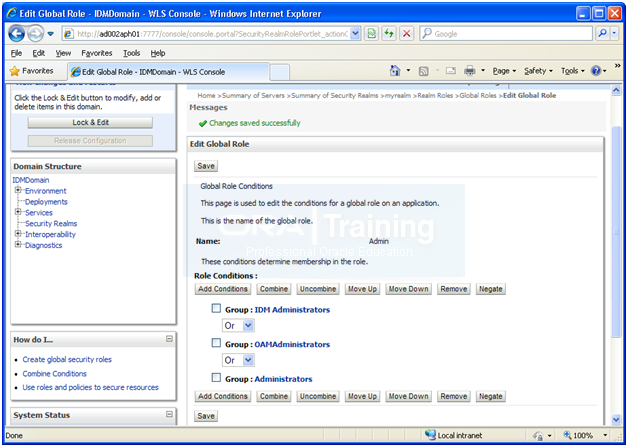
Perform Bug 13824816 Workaround
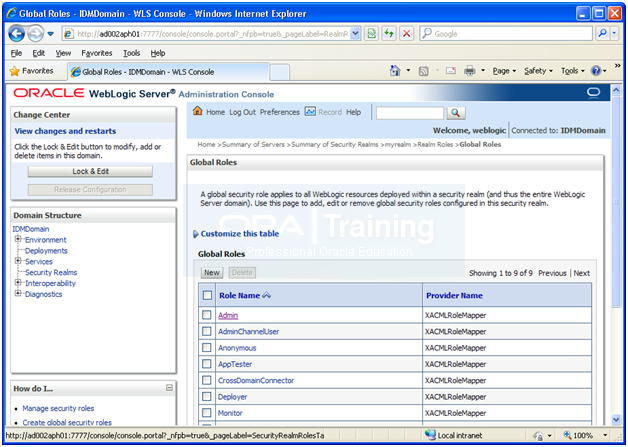
http://<hostname>:7777/console
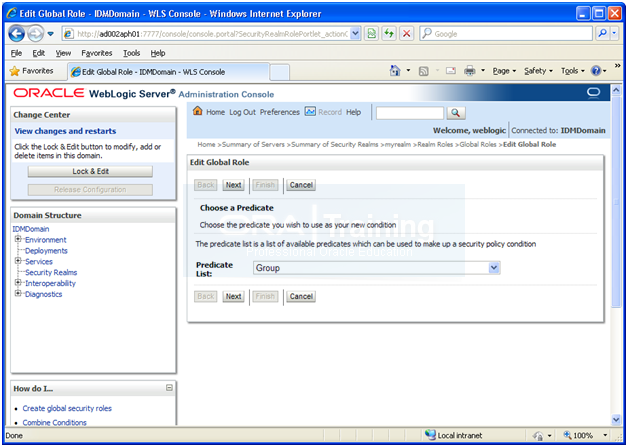
Security Realm->myrealm->Roles and Policies -> Expand Global Roles -> Click on Roles
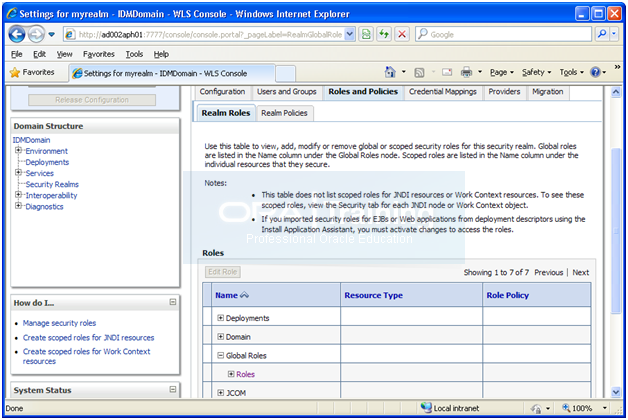
Expand Global Roles. Click on Roles
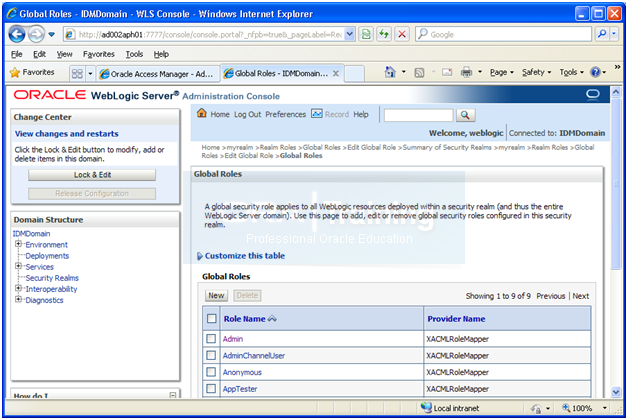
Click on Admin
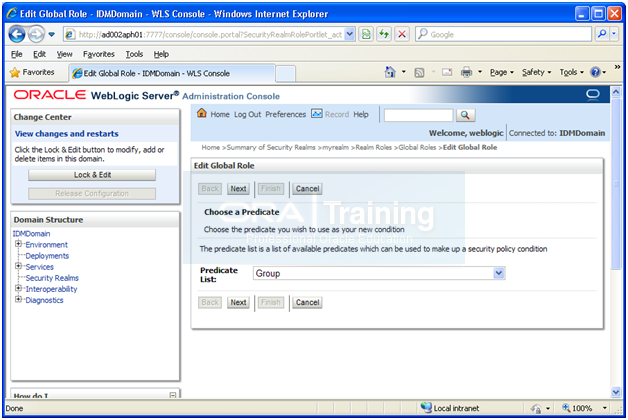
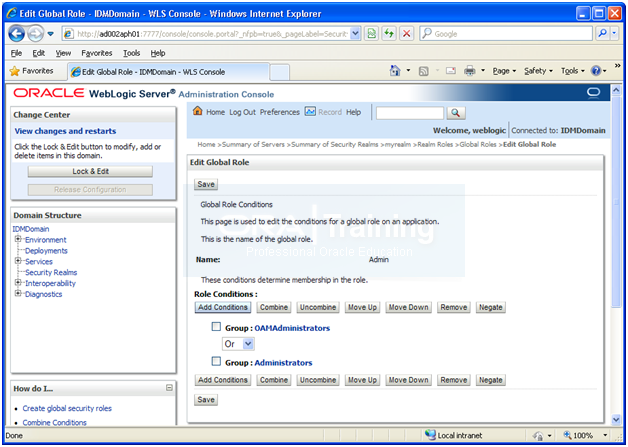
Click Next
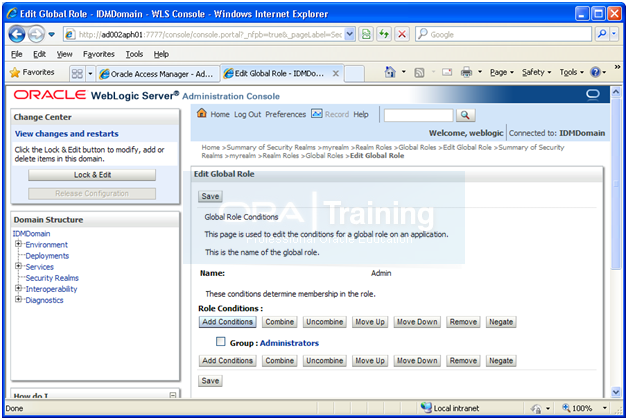
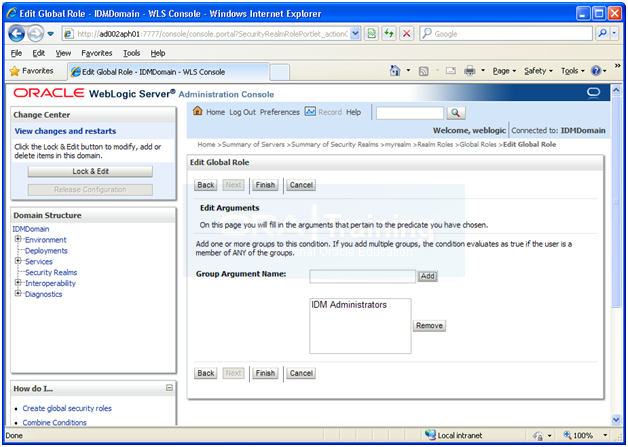
Click on Add conditions
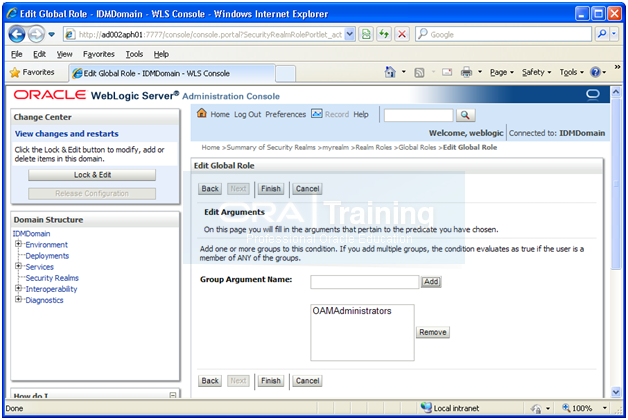
Enter OAMAdministrators in text-box and click Add
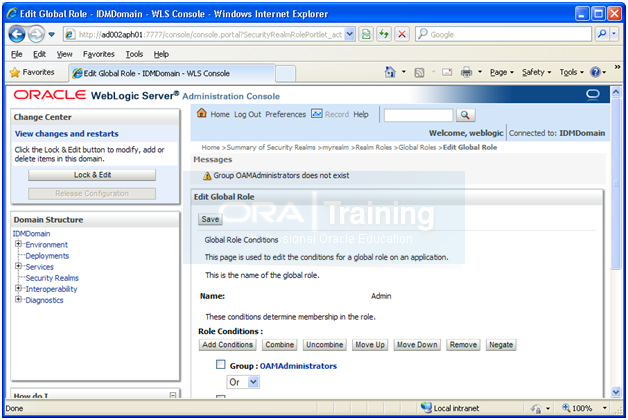
Click Save
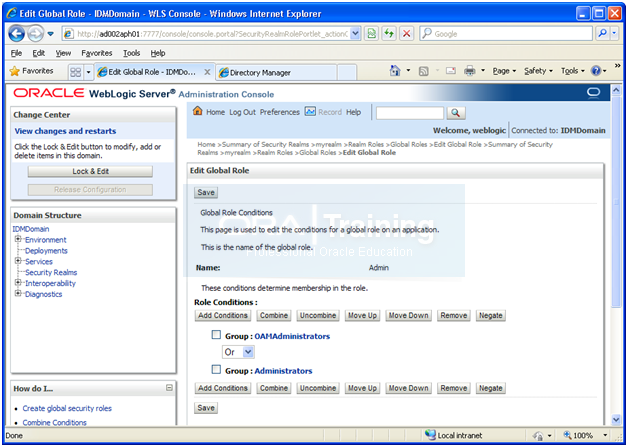
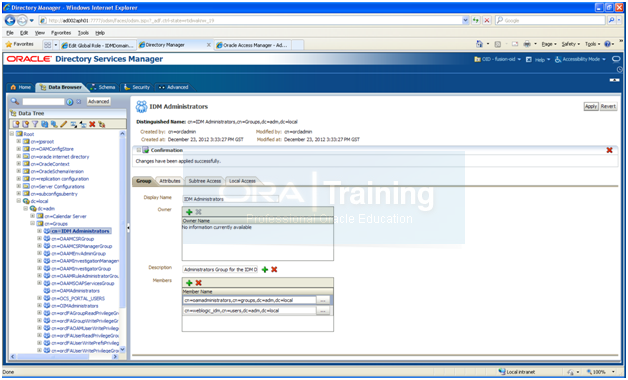
Note: Following is not required as per the “latest” document but for the safe side adding this as well.
1. Open http://<hostname>:7777/odsm
2. Connect to a directory instance.
3. Click the Data Browser tab.
4. Expand the Client View entry in the directory tree (dc=<domain>) then expand cn=Groups.
5. Click IDMAdministrators.
6. In the Members box, click + to add a new entry.
7. Enter cn=oamadministrators,cn=groups,dc=adm,dc=local
8. Click Apply.
Adding the oamadmin Account to Access System Administrators
The oamadmin user is assigned to the Oracle Access Manager Administrators group, which is in turn assigned to the Access System Administrators group. Fusion Applications, however, requires the oamadmin user to be explicitly added to that role.
To do this, perform the following steps:
1. Log in to the oamconsole at http://<hostname>:7777/oamconsole
2. Click the System Configuration tab.
3. Expand Data Sources – User Identity Stores.
4. Click OIMIDStore.
5. Click Open.
6. Click the + symbol next to Access System Adminsitrators.
7. Type oamadmin in the search box and click Search.
8. Click the returned oamadmin row, then click Add Selected.
9. Click Apply.
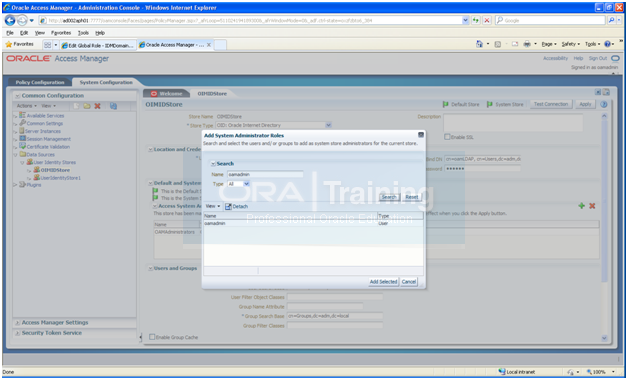
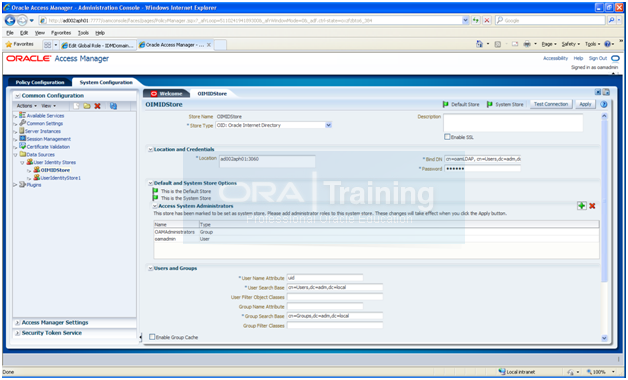
Click Apply.
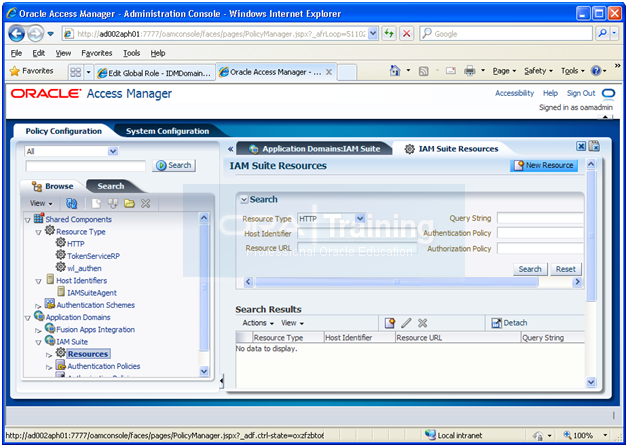
Create Oracle Access Manager Policies for WebGate 11g
In order to allow WebGate 11g to display the credential collector, you must add /oam to the list of public policies.
Proceed as follows:
1. Log in to the OAM console
2. Select the Policy Configuration tab.
3. Expand Application Domains – IAM Suite
4. Click Resources.
5. Click Open.
6. Click New resource.
7. Provide the following values:
Type: HTTP
Description: OAM Credential Collector
Host Identifier: IAMSuiteAgent
Resource URL: /oam
Protection Level: Unprotected
Authentication Policy: Public Policy
8. Click Apply.
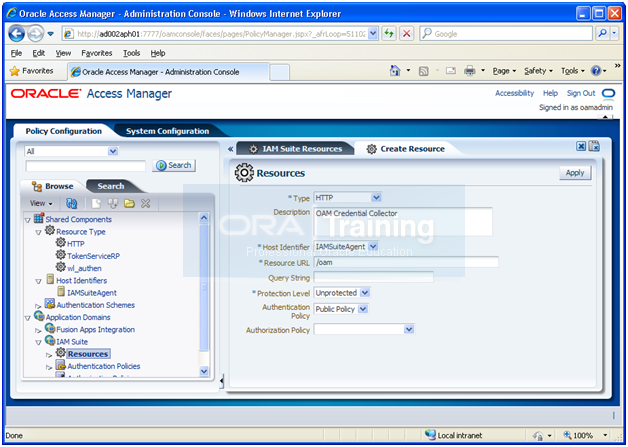
Click Apply
Validate OAM
Note: The OAM validation tool is now no longer used for Solaris since current latest documentation
Following is given for reference only. This is not required for Solaris due to bug mentioned below. It will work for Linux without any issues.
-bash-3.2$ export JAVA_HOME=/app/fusion/jdk6
-bash-3.2$ export PATH=$JAVA_HOME/bin:$PATH
-bash-3.2$ cd /app/fusion/fmw/iam/oam/server/tester/
-bash-3.2$ java -jar oamtest.jar
It will throw above error due to a bug in this tool in Solaris
The fix is to temporarily remove Password from Webgate through oamadmin
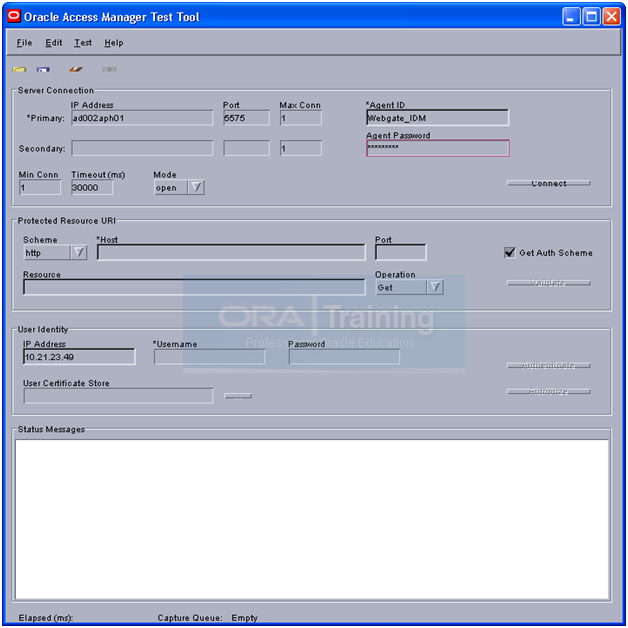
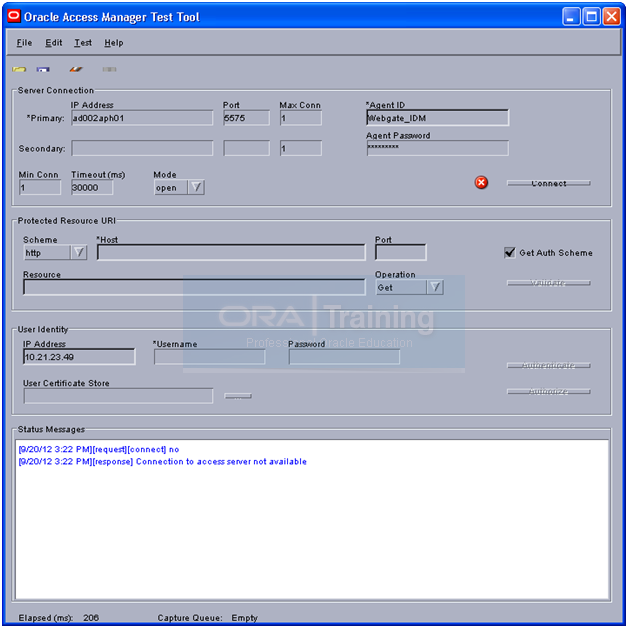
It will throw above error due to a bug in this tool on Solaris Platform. On Linux/Windows it will succeed.
The fix is to temporarily remove Password from Webgate through oamadmin (Careful to revert it later). We suggest not to run this tool at all in Solaris.
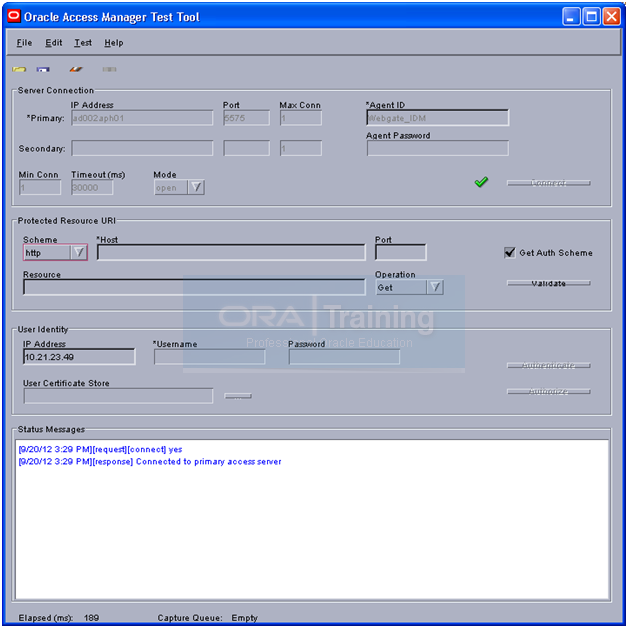
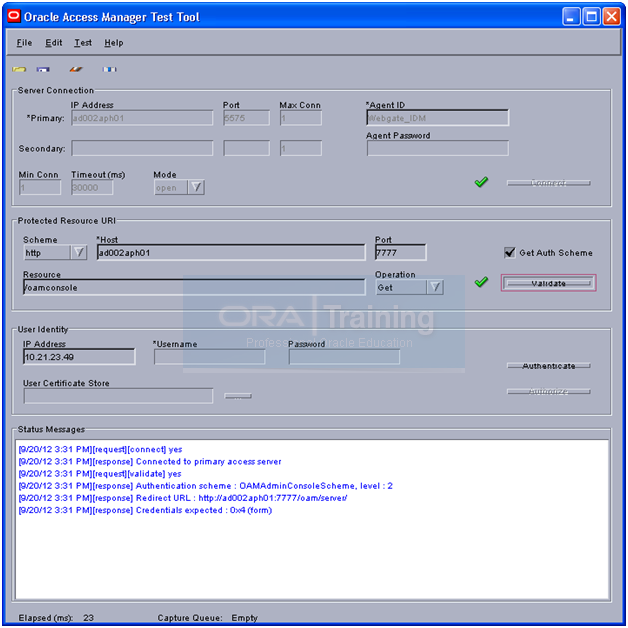
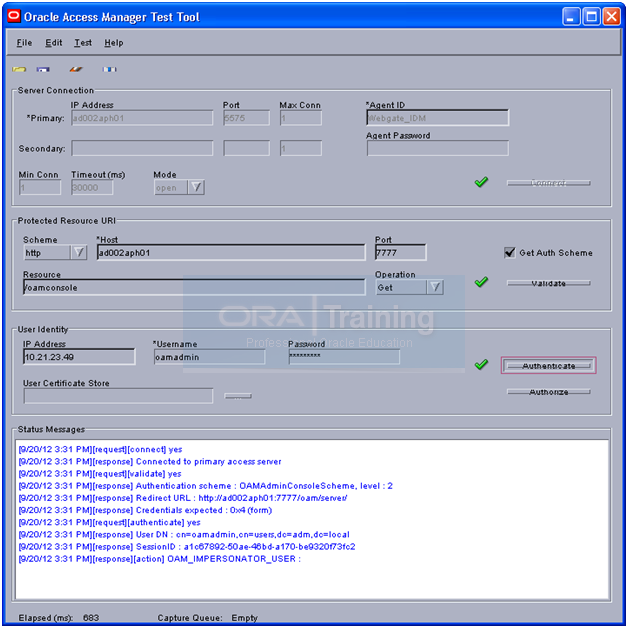
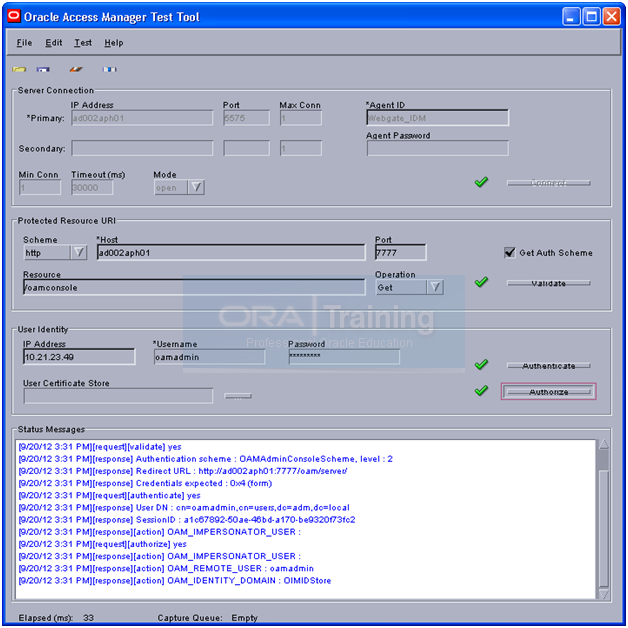
Put the password back. (If you have changed in previous step)
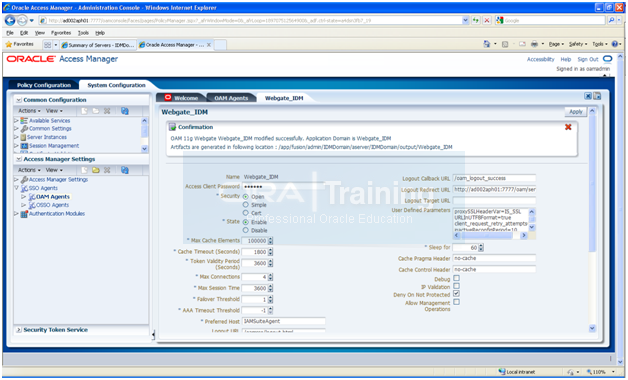
Updating Oracle Access Manager System Parameters
Change to following.
Session Lifetime: 120
Idle timeout (Minutes): 120
Maximum number of connections per user: 200
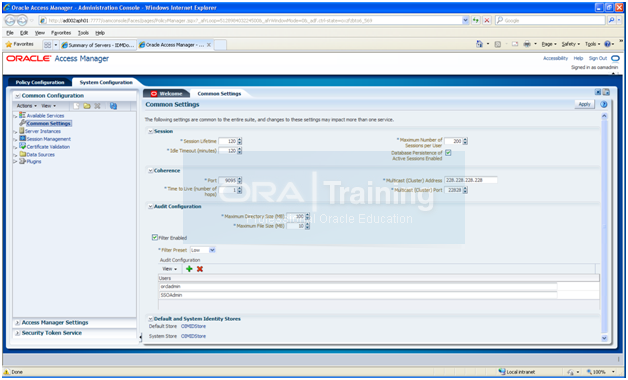
This will automatically edit and change the values in /app/fusion/admin/IDMDomain/aserver/IDMDomain/config/fmwconfig/oam-config.xml
Please note that we are not changing the value for “NoUniqueSessionsFor10gAgents“ since it is not mentioned in the latest documentation.
Restart OAM
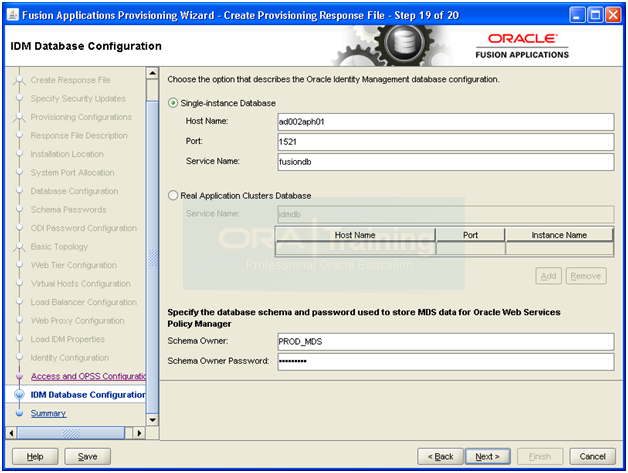
Configure Oracle Identity Manager (OIM) and Oracle SOA Suite
Start the configuration from <IAM_HOME>/bin
-bash-3.2$ cd /app/fusion/fmw/iam/bin/
-bash-3.2$ ./config.sh &
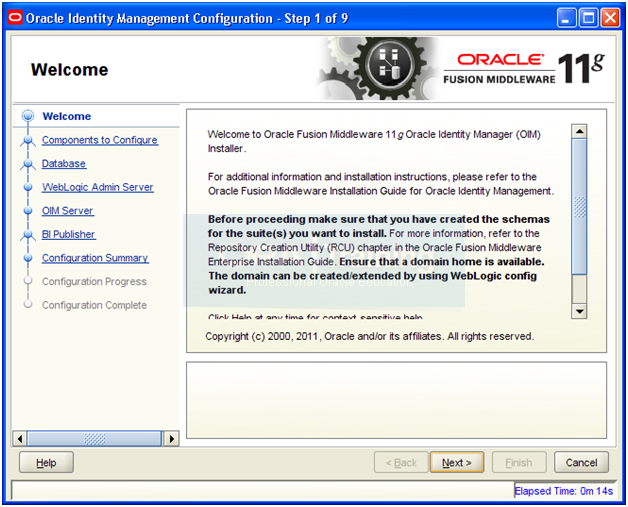
Click Next

Select only “OIM Server” and click Next
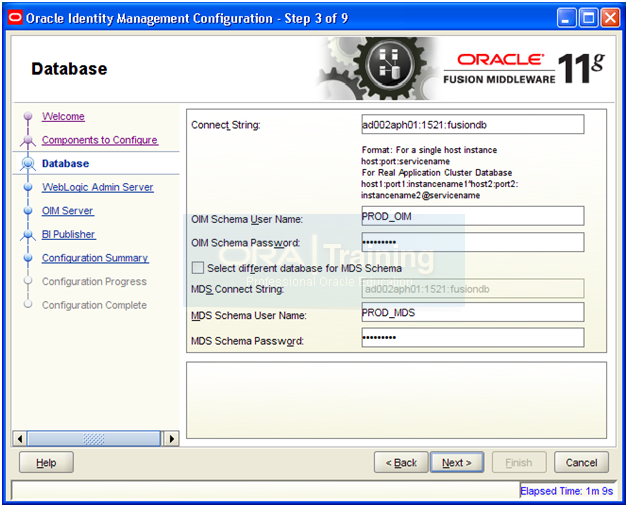
Enter database details. Make sure to use correct prefix as we selected earlier (in our case PROD). Click Next
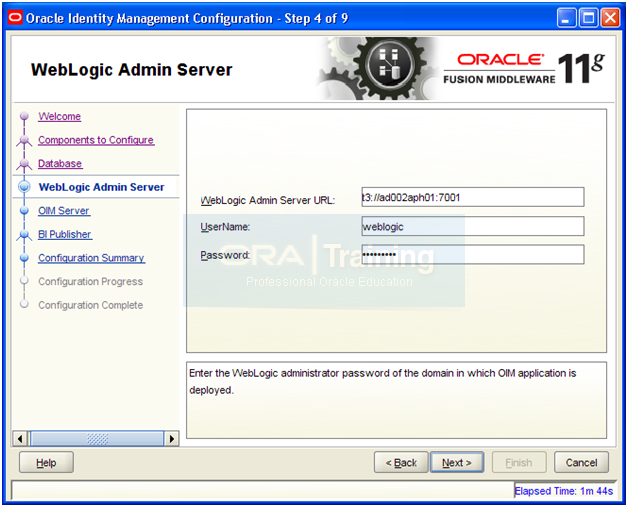
Admin server URL: t3://<hostname>:7001
Username and password of weblogic user
Click Next
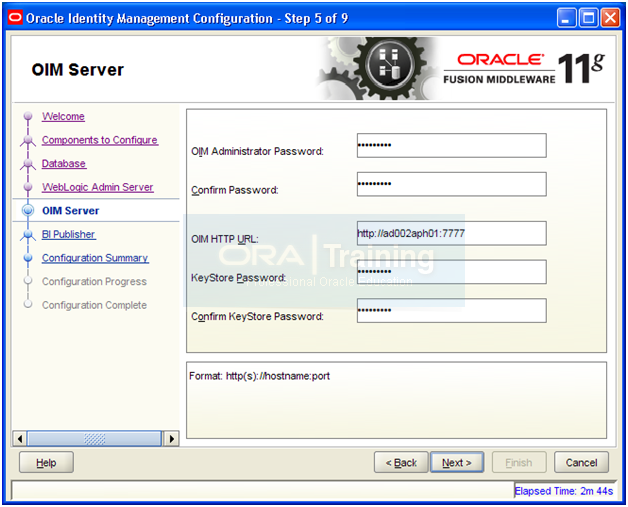
Enter required password and OIM HTTP URL as http://<hostname>:7777
Click Next
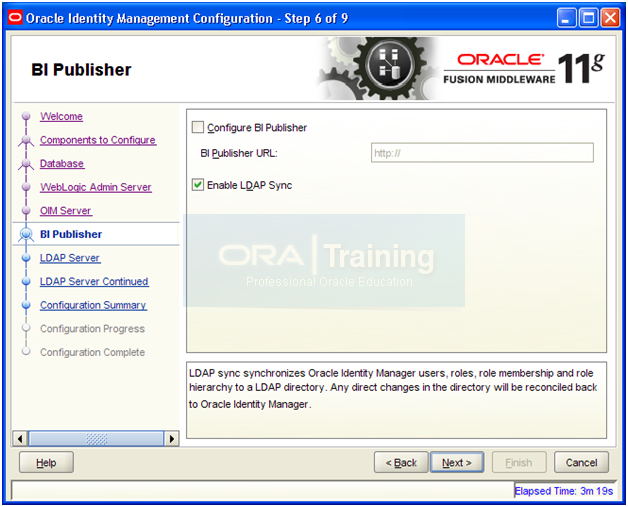
Check “Enable LDAP Sync” and click Next
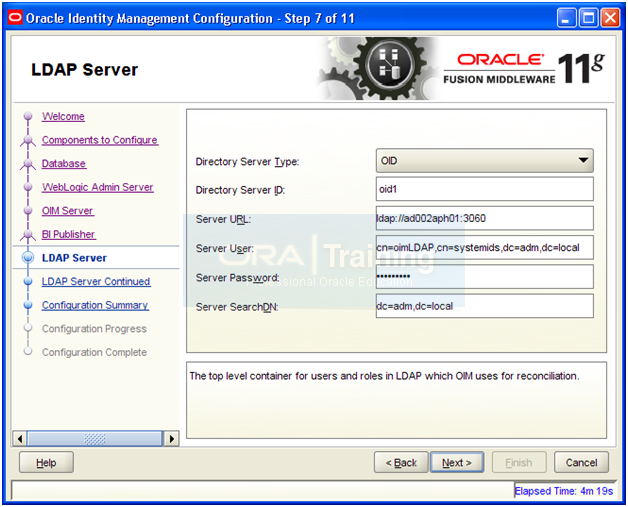
Enter following values
Directory Server Type: OID
ID: oid1
URL: ldap://<hostname>:3060
User: cn=oimLDAP,cn=systemids,dc=<domain>,dc=<com>
Click Next
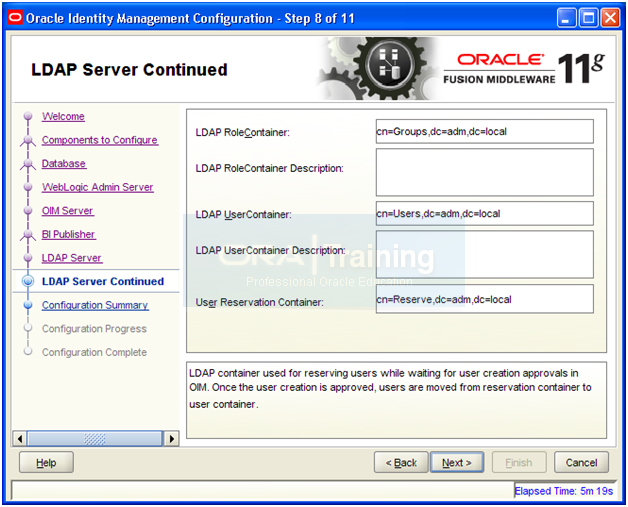
Enter following values
Role Container: cn=Groups,dc=<domain>,dc=<com>
User Container: cn=Users,dc=<domain>,dc=<com>
Reservation Container: cn=Reserve,dc=<domain>,dc=<com>
Click Next
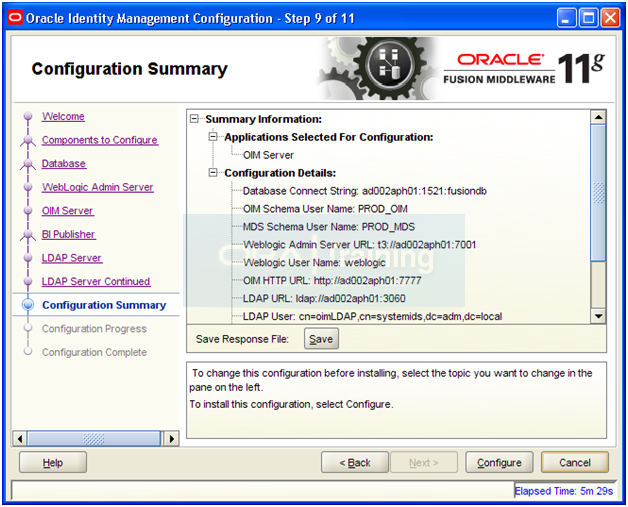
Review summary and click Configure

Once configure completes, click Next
Review and click Finish
Note: If instead of above screen you see following error then you have missed a major patch 13399365.
“Config Action Oracle Identity Manager Configuration failed“.
The errors in .out file
java.lang.NoSuchMethodError: oracle.jdbc.OracleConnection.setApplicationContext(Ljava/lang/String;Ljava/lang/String;Ljava/lang/String;)V
java.lang.IllegalStateException: Action:OIM Configuration failed with error:interrupted
As per Oralce metalink note This is due to bug 14125012�
Mismatched Components Version Cause Config.sh To Fail on Configure Oracle Identity Manager with Fusion Applications [ID 1467992.1]
This is because the certified version of OAM with 11.1.4 applications is 11.1.1.5.2 while the supplied version is 11.1.1.5.0 so we need to apply patches to upgrade this version.
The patches are mentioned in the release notes as well as available in /app/stage/installers/iam/patch directory. Please apply them to fix this. We have a shortcut workaround to copy the required files only from patch. But this is not recommended so we will not post here. Just to let the geeks know J
Stop Admin server and all managed servers and then start all servers including wls_soa1 and wls_oim1
Test OIM and SOA using following URLS
and
http://<hostname>:8001/soa-infra
Note: If you get 404 error for OIM or if you see following errors in OIM log files (even if OIM status shows as “RUNNING” in admin console) then OIM has not come up properly. You can see this in EM and it will show OIM as down.
<Error> <Deployer> <BEA-149265> <Failure occurred in the execution of deployment request with ID ‘1356332711618’ for task ‘1’. Error is: ‘weblogic.management.DeploymentException: [J2EE:160149]Error while processing library references. Unresolved application library references, defined in weblogic-application.xml: [Extension-Name: oracle.sdp.client, exact-match: false].’
weblogic.management.DeploymentException: [J2EE:160149]Error while processing library references. Unresolved application library references, defined in weblogic-application.xml: [Extension-Name: oracle.sdp.client, exact-match: false].
at weblogic.application.internal.flow.CheckLibraryReferenceFlow.prepare(CheckLibraryReferenceFlow.java:26)
at weblogic.application.internal.BaseDeployment$1.next(BaseDeployment.java:648)
at weblogic.application.utils.StateMachineDriver.nextState(StateMachineDriver.java:52)
at weblogic.application.internal.BaseDeployment.prepare(BaseDeployment.java:191)
at weblogic.application.internal.EarDeployment.prepare(EarDeployment.java:59)
Truncated. see log file for complete stacktrace
As per metalink Note: 1328471.1 following needs to be done to fix this.
Admin console->Deplyments->go to oracle.sdp.client page
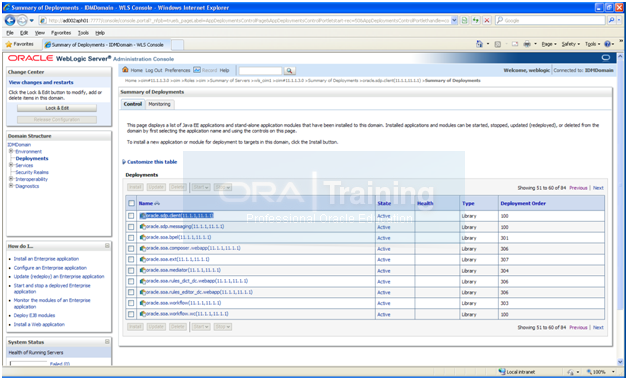
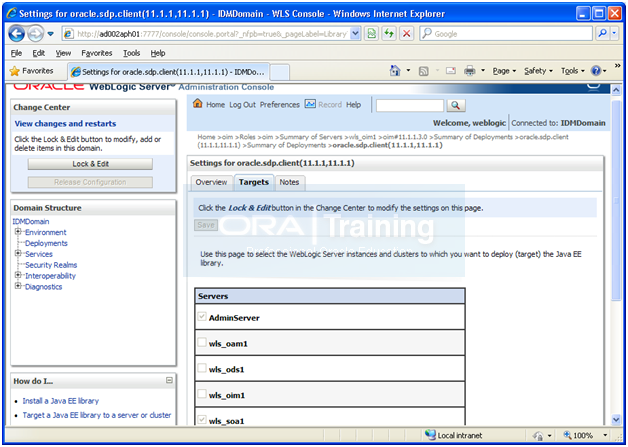
Click on Targets. You will see that the checkbox for wls_oim1 is not selected.
Lock & Edit and select the checkbox and Activate changes.
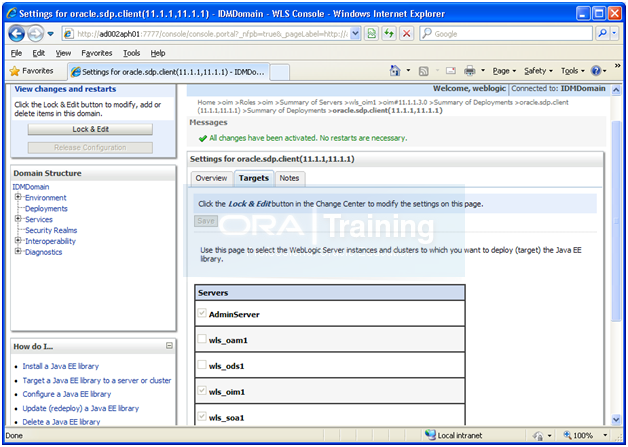
Restart OIM
Validate OIM
Launch URL http://<hostname>:14000/oim
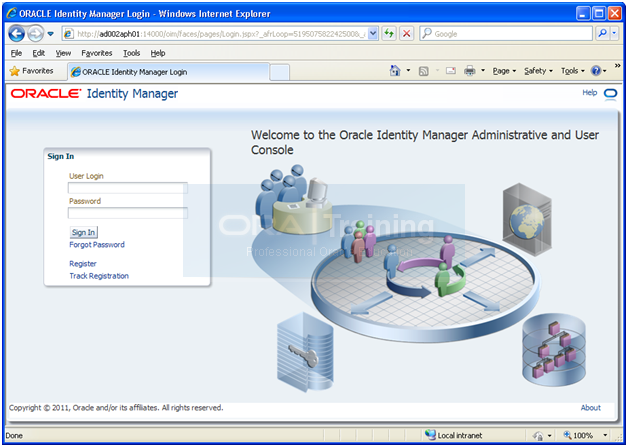
Login with xelsysadm user
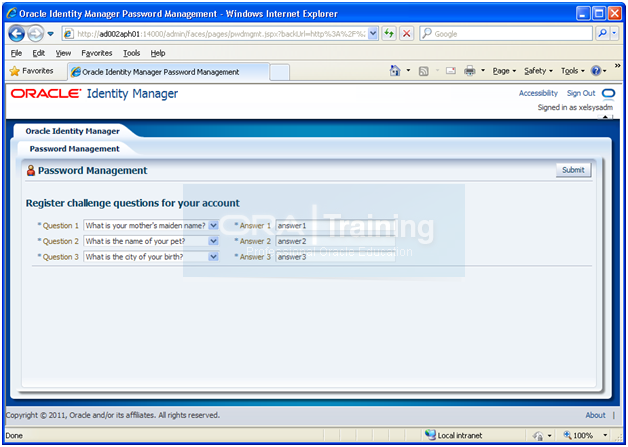
If you have not applied post-steps for patch 13399365 properly then you might get following errors.
oracle.iam.platform.kernel.OrchestatrionException
“ADF_FACES-60097 : For more information, please see the server’s error log for an entry beginning with: ADF_FACES-60096: Server Exception during PPR, #8″
Internal Exception: java.sql.SQLSyntaxErrorException: ORA-00904: “CONTEXTVAL”: invalid identifier
Error Code: 904
Call: INSERT INTO ORCHPROCESS (ID, BULKPARENTID, CHANGETYPE, CONTEXTVAL, CREATEDON, ENTITYID, ENTITYTYPE, MODIFIEDON, OPERATION, ORCHESTRATION, ORCHTARGET, PARENTPROCESSID, RETRY, SEQUENCE, STAGE, STATUS) VALUES (?, ?, ?, ?, ?, ?, ?, ?, ?, ?, ?, ?, ?, ?, ?, ?)
bind => [16 parameters bound]
This is because following column might not be available in PROD_OIM. ORCHPROCESS table. The post steps for above patch create this column.
CONTEXTVAL CLOB
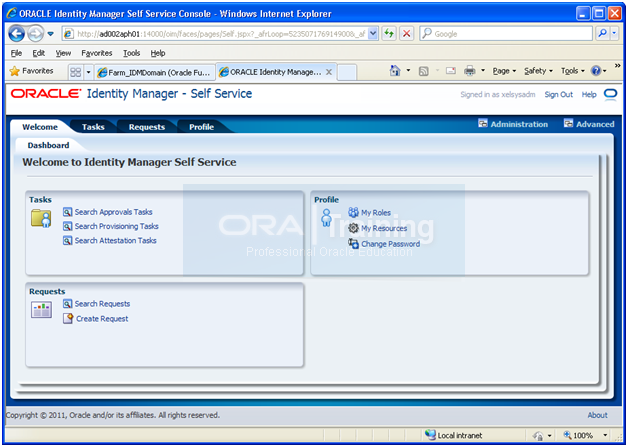
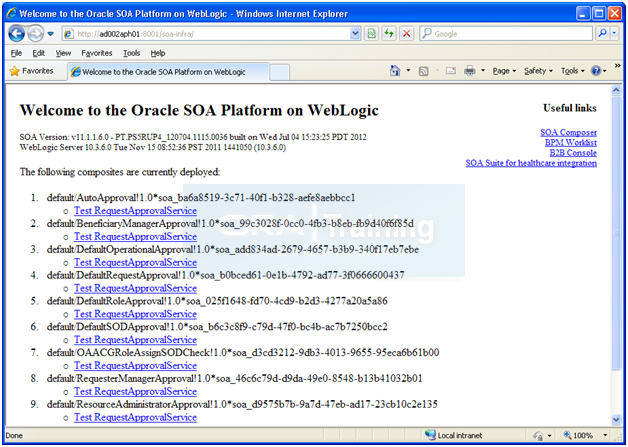
Validate SOA
Launch URL http://<hostname>:8001/soa-infra
Login with weblogic user
Prepare OIM to reconcile from ID store
-bash-3.2$ cd /app/fusion/fmw/iam/server/ldap_config_util/
Make backup of existing ldapconfig.props file
-bash-3.2$ cp -pr ldapconfig.props ldapconfig.props_orig
Modify ldapconfig.props
-bash-3.2$ more ldapconfig.props
# OIMServer Type, Valid values can be WLS, JBOSS, WAS
# e.g.: OIMServerType=WLS
OIMServerType=WLS
# OIMAdmin User Login
# e.g.: OIMAdminUser=xelsysadm
OIMAdminUser=xelsysadm
# Skip Validation of OVD Schema
# e.g.: SkipOVDValidation=true|false, Default false
SkipOVDValidation=true
# OIM Provider URL
# e.g.: OIMProviderURL=t3://localhost:8003
OIMProviderURL=t3://ad002aph01:14000
# OID URL
# e.g.: OIDURL=ldap://localhost:389
OIDURL=ldap://ad002aph01:3060
# Admin user name to connect to OID
# e.g.: OIDAdminUsername=cn=orcladmin
OIDAdminUsername=cn=oimLDAP,cn=systemids,dc=adm,dc=local
# Search base
# e.g.: OIDSearchBase=dc=company,dc=com
OIDSearchBase=dc=adm,dc=local
# Name of the user container
# e.g.: UserContainerName=cn=Users
UserContainerName=cn=Users
# Name of the role container
# e.g.: RoleContainerName=cn=Roles
RoleContainerName=cn=Groups
# Name of the reservation container
# e.g.: ReservationContainerName=cn=Reserve
ReservationContainerName=cn=Reserve
Source environment
-bash-3.2$ export JAVA_HOME=/app/fusion/jdk6
-bash-3.2$ export WL_HOME=/app/fusion/fmw/wlserver_10.3
Run following command
-bash-3.2$ ./LDAPConfigPostSetup.sh
[Enter OID admin password:]
[Enter OIM admin password:]
Successfully Enabled Changelog based Reconciliation schedule jobs
Configure HTTP for OIM and SOA
Add following entries in /app/fusion/admin/ohs_inst1/config/OHS/ohs1/moduleconf/admin.conf
# oim admin console(idmshell based)
<Location /admin>
SetHandler weblogic-handler
WLProxySSL OFF
WLProxySSLPassThrough OFF
WLCookieName oimjsessionid
WebLogicHost ad002aph01
WebLogicPort 14000
WLLogFile “${ORACLE_INSTANCE}/diagnostics/logs/mod_wl/oim_component.log”
</Location>
# oim self and advanced admin webapp consoles(canonic webapp)
<Location /oim>
SetHandler weblogic-handler
WLProxySSL OFF
WLProxySSLPassThrough OFF
WLCookieName oimjsessionid
WebLogicHost ad002aph01
WebLogicPort 14000
WLLogFile “${ORACLE_INSTANCE}/diagnostics/logs/mod_wl/oim_component.log”
</Location>
# SOA Callback webservice for SOD – Provide the SOA Managed Server Ports
<Location /sodcheck>
SetHandler weblogic-handler
WLProxySSL OFF
WLProxySSLPassThrough OFF
WLCookieName oimjsessionid
WebLogicHost ad002aph01
WebLogicPort 8001
WLLogFile “${ORACLE_INSTANCE}/diagnostics/logs/mod_wl/oim_component.log”
</Location>
# Callback webservice for SOA. SOA calls this when a request is approved/rejected
# Provide the SOA Managed Server Port
<Location /workflowservice>
SetHandler weblogic-handler
WLProxySSL OFF
WLProxySSLPassThrough OFF
WLCookieName oimjsessionid
WebLogicHost ad002aph01
WebLogicPort 14000
WLLogFile “${ORACLE_INSTANCE}/diagnostics/logs/mod_wl/oim_component.log”
</Location>
# xlWebApp – Legacy 9.x webapp (struts based)
<Location /xlWebApp>
SetHandler weblogic-handler
WLProxySSL OFF
WLProxySSLPassThrough OFF
WLCookieName oimjsessionid
WebLogicHost ad002aph01
WebLogicPort 14000
WLLogFile “${ORACLE_INSTANCE}/diagnostics/logs/mod_wl/oim_component.log”
</Location>
# Nexaweb WebApp – used for workflow designer and DM
<Location /Nexaweb>
SetHandler weblogic-handler
WLProxySSL OFF
WLProxySSLPassThrough OFF
WLCookieName oimjsessionid
WebLogicHost ad002aph01
WebLogicPort 14000
WLLogFile “${ORACLE_INSTANCE}/diagnostics/logs/mod_wl/oim_component.log”
</Location>
# used for FA Callback service.
<Location /callbackResponseService>
SetHandler weblogic-handler
WLProxySSL OFF
WLProxySSLPassThrough OFF
WLCookieName oimjsessionid
WebLogicHost ad002aph01
WebLogicPort 14000
WLLogFile “${ORACLE_INSTANCE}/diagnostics/logs/mod_wl/oim_component.log”
</Location>
# spml xsd profile
<Location /spml-xsd>
SetHandler weblogic-handler
WLProxySSL OFF
WLProxySSLPassThrough OFF
WLCookieName oimjsessionid
WebLogicHost ad002aph01
WebLogicPort 14000
WLLogFile “${ORACLE_INSTANCE}/diagnostics/logs/mod_wl/oim_component.log”
</Location>
<Location /HTTPClnt>
SetHandler weblogic-handler
WLProxySSL OFF
WLProxySSLPassThrough OFF
WLCookieName oimjsessionid
WebLogicHost ad002aph01
WebLogicPort 14000
WLLogFile “${ORACLE_INSTANCE}/diagnostics/logs/mod_wl/oim_component.log”
</Location>
# role-sod profile
<Location /role-sod>
SetHandler weblogic-handler
WLCookieName oimjsessionid
WebLogicHost ad002aph01
WebLogicPort 14000
WLLogFile “${ORACLE_INSTANCE}/diagnostics/logs/mod_wl/oim_component.log”
</Location>
# SOA Infrastructure
<Location /soa-infra>
SetHandler weblogic-handler
WLCookieName oimjsessionid
WebLogicHost ad002aph01
WebLogicPort 8001
WLLogFile “${ORACLE_INSTANCE}/diagnostics/logs/mod_wl/oim_component.log”
</Location>
# UMS Email Support
<Location /ucs>
SetHandler weblogic-handler
WLCookieName oimjsessionid
WebLogicHost ad002aph01
WebLogicPort 8001
WLLogFile “${ORACLE_INSTANCE}/diagnostics/logs/mod_wl/oim_component.log”
</Location>
-bash-3.2$ /app/fusion/admin/ohs_inst1/bin/opmnctl stopall
opmnctl stopall: stopping opmn and all managed processes…
-bash-3.2$ /app/fusion/admin/ohs_inst1/bin/opmnctl startall
opmnctl startall: starting opmn and all managed processes…
Now login to Weblogic Console at http://<hostname>:7777/console
Change Host assertion in Weblogic
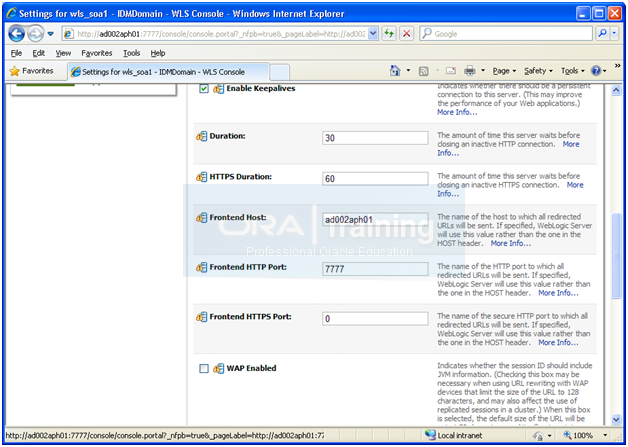
Click Save and Activate Changes.
Validate OIM and SOA using HTTP port
http://<hostname>:7777/soa-infra
Enabling Oracle Identity Manager to Connect to SOA Using the Administrative Users Provisioned in LDAP
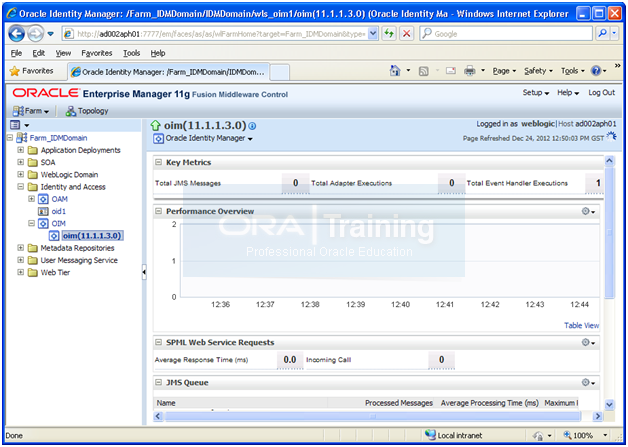
Login to EM console
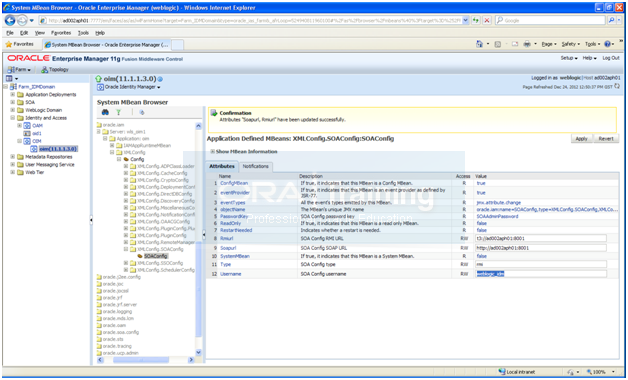
Select Farm_IDMDomain –> Identity and Access–> OIM –> oim(11.1.1.3.0).
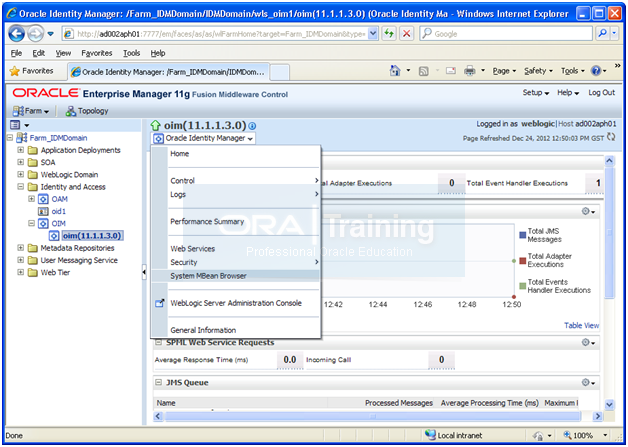
Select MBean Browser from the menu or right click to select it.
Select Application defined Mbeans –> oracle.iam –> Server: wls_oim1 –> Application: oim –> XML Config -> Config –> XMLConfig.SOAConfig –>SOAConfig
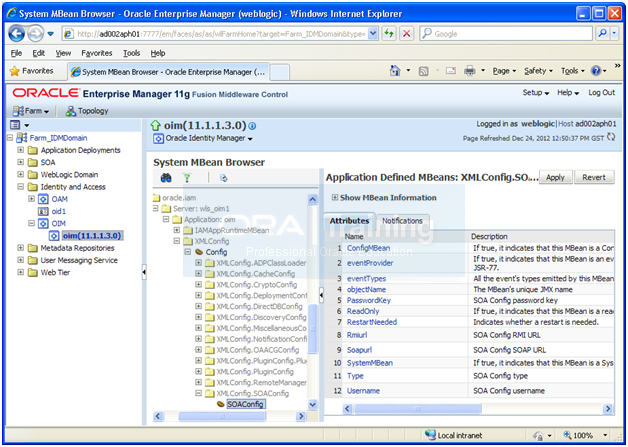
Change the username attribute to weblogic_idm
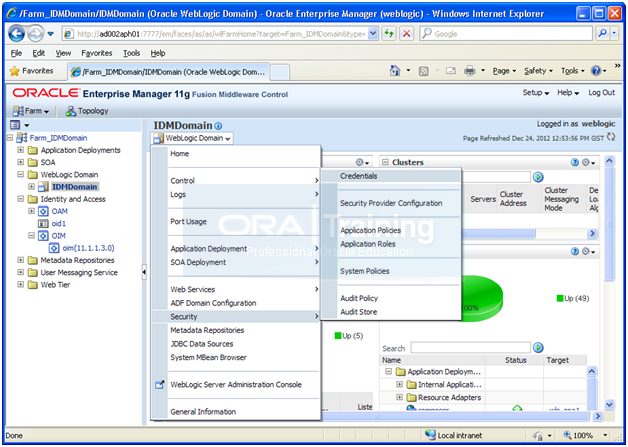
select Weblogic Domain –> IDMDomain from the Navigator.
Select Security –> Credentials from the down menu
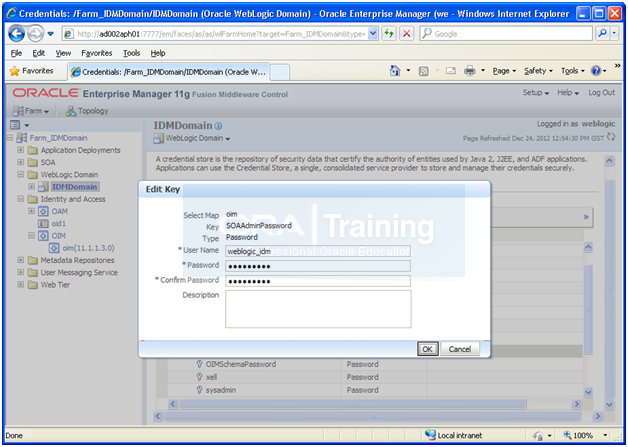
Expand the key oim.
Click SOAAdminPassword.
Click Edit.
Change the username to weblogic_idm and set the password to the accounts password.
Click OK.
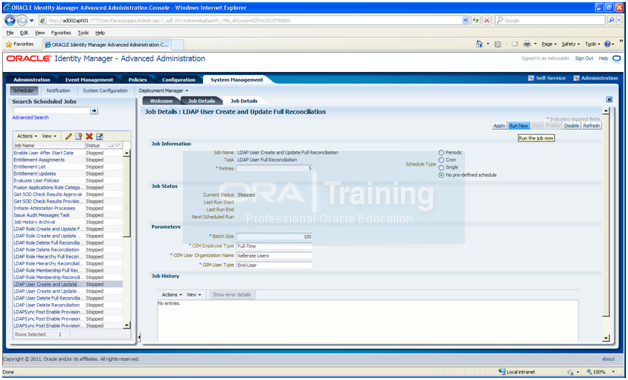
Run the reconciliation process to enable the Oracle WebLogic Server administrator, weblogic_idm, to be visible in the OIM Console. Follow these steps:
a. Log in to Oracle Identity Manager at:
https://sso.mycompany.com:443/oim as the user xelsysadm.
b. If prompted, set up challenge questions. This happens on your first login to Oracle Identity Manager.
c. Click Advanced.
d. Click the System Management tab.
e. Click the arrow for the Search Scheduled Jobs to list all the schedulers.
f. Select LDAP User Create and Update Full Reconciliation.
g. Click Run Now to run the job.
h. Go to the Administration page and perform a search to verify that the user is visible in the Oracle Identity Manager console.
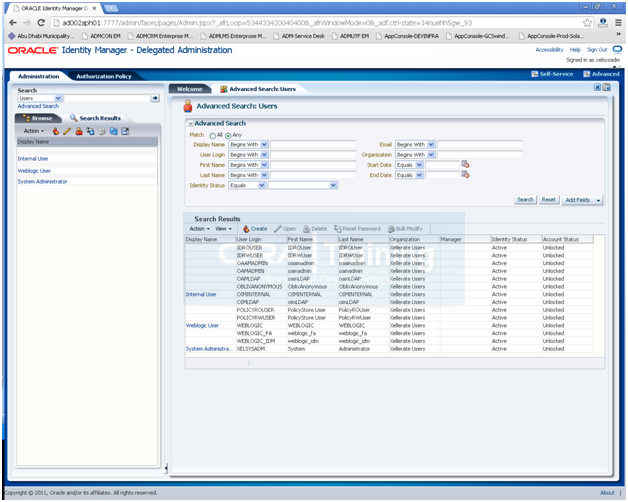
Select Administration. Click Advanced Search –> Roles
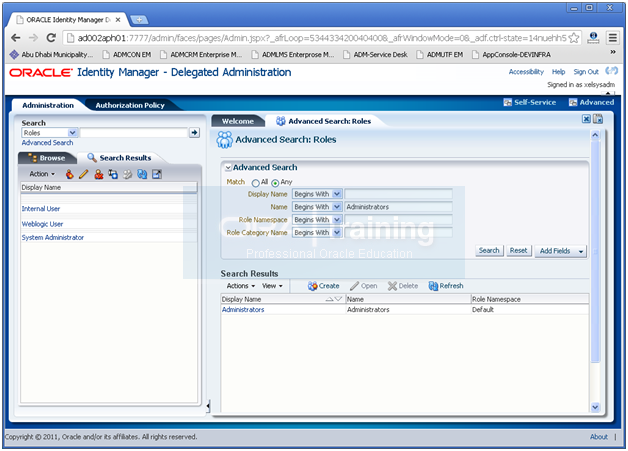
Search for the Administrators role. Click the Administrators Role.
Click Open.
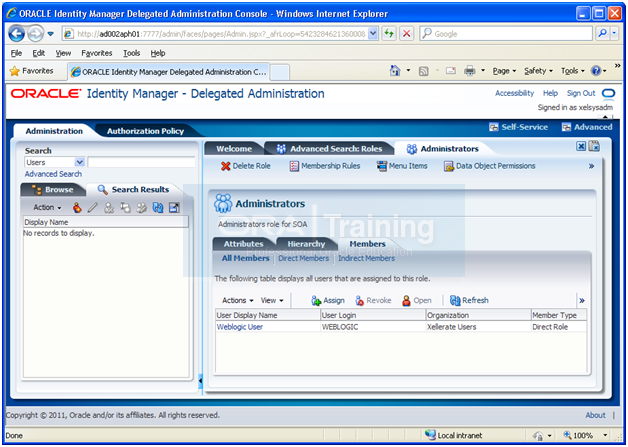
Click the Members tab. Click Assign.
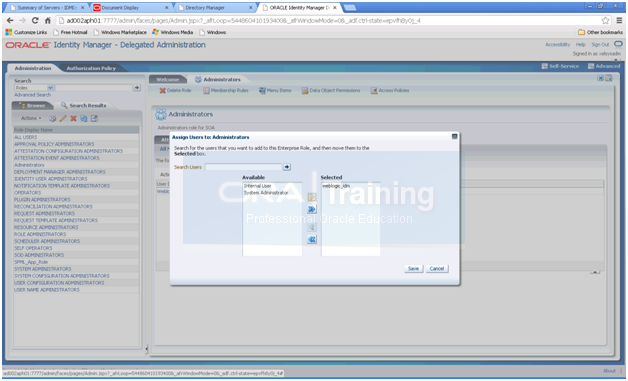
Type weblogic_idm in the Search box and Click ->.
Select weblogic_idm from the list of available users.
Click > to move to Selected Users.
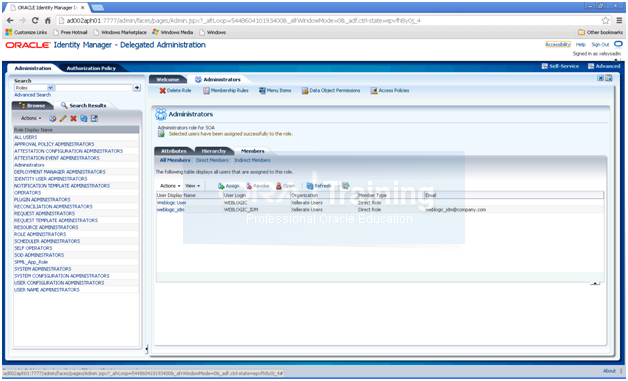
Click Save.
Restart Oracle Identity Manager managed server.
Installing Oracle Fusion Applications – steps
-
Create another database for Oracle Identity Management Infrastructure (optional)
Next: Integrate Oracle Identity Manager (OIM) and Oracle Access Manager (OAM)

Recent Comments